Did you ever consider what your computer does to know the direction in which it should forward your data through the internet? The whole thing works through a state of art subnetting system that incorporates quite a number of interesting procedures. Imagine heading to a city where streets are assembled as a network connecting different areas. It is as if the computer tells with the help of street signs to which ‘neighborhood’ it belongs to of the entire cyberspace.
What is a Subnet Mask?
Just as every house has an address every machine that is connected to the internet has an address known as its IP address. A subnet mask works as a discriminator: it divides your IP address horizontally: that is the neighborhood or the network identification and the house or household identification where computers will be able to route traffic or communicate with other devices within that network.
The Old Way: Classful Addressing
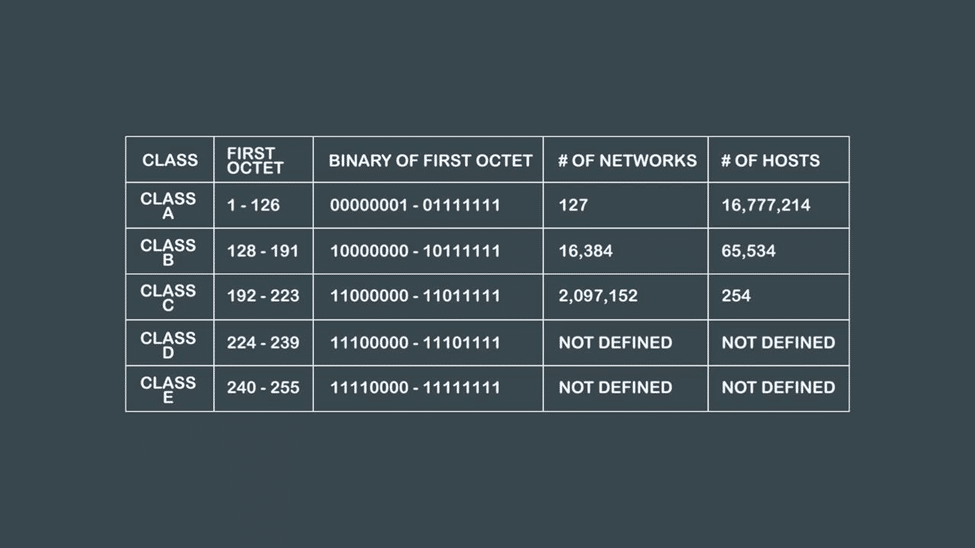
Originally, when the concept of IP address came into existence, the addresses were clearly categorized into three classes A, B, and C and were assigned a default subnet mask. This was like having strict set down regulations on every region of the city.
The Modern Way: CIDR
Today there is CIDR, Classless Inter-Domain Routing, which is seen as more flexible. CIDR, on the other hand, uses smaller subnet masks, which are customized rather than having different sized neighborhoods and road systems. This more wisely utilizes Internet addresses and enhances the overall network performance.
Why Are These Subnet Masks So Important?
Just like clear street signs help traffic flow smoothly in a city, subnet masks are essential for keeping internet traffic organized:
Traffic Cops:
Subnet masks help in directing routers, which can be viewed more as traffic directions ensuring Internet traffic gets to the right place.
Broadcast Control:
It assists in controlling the number of broadcast messages so that needless notice and crowding on the network are avoided.
Security Shield:
Networks for this reason divided into segments and provide security levels so as to ensure that hackers cannot be able to implement their planned manipulations.
IP Address Efficiency:
The feature of Flexible subnetting allows for management of exposure of a certain IP address so that all network devices acquire their address.
Easy Troubleshoot:
Whenever there are issues on trying to connect online, the subnet masks assist by giving recommendations that point to the specific level of complication.
Masks of this kind: How do they actually work?
It might sound technical, but the process is surprisingly straightforward:
Binary Code:
The IP address and the subnet mask are also converted into binary form that is a combination of two numbers 0’s and 1’s.
The “AND” Operation:
The IP address and the subnet mask together with the IP address go through a process known as “bitwise AND”.
Neighborhood Identified:
This operation uncovers the network ID, which in effect gives the exact ‘neighborhood’ that the particular device is aligned to in the larger internet environ
Beyond Default Subnet Masks: The World of VLSM
However, default subnet masks have not been sufficient for advanced networking over the last two decades and more. VLSM gives capability to divide the subnet into different portions with different subnet masks but same IP address range. It is like having cities within the nation which may have different sizes and blocks of streets with best allocation of resources enhancing the general efficiency of the connections of the network.
Exploring Subnetting in IPv6
This impact diverted people’s focus on IPv4 as compared to IPv6 subnetting. IPv6 actually incorporates a 128-bit addressing scheme, while IPv4 has a 32-bit addressing system. Unlike in IPv4, in IPv6, one can practically use as many numeric addressing schemes as he or she wants. In IPv6, it is also possible to do a subnetting but whether it by using a prefix length it can be identified as easier in a way of handling larger networks without having an address space problem.
General Problems in Subnetting
Despite its advantages, subnetting can present challenges, particularly for network administrators:
Complex Calculations: Actually, identifying the certain subnet masks needed for a particular case is more or less a big challenge and lengthy process.
Risk of Errors: One wrong move could slow down the use of the network or even cause an outage with the correct setup of these subnet masks.
Scalability Issues: Lack of planning can lead to subnets’ structure that is difficult to extend and change.
A Guide to Subnetting: Strategies, Products and Services
To overcome these challenges, various tools and best practices can help:
Subnet Calculators: Web-based applications that help lessen the chances of messing up with numbers.
Detailed Network Documentation: This way it is easier to manage and troubleshoot subnet structures because records are kept accurately.
Regular Training: This means that it enables the administrators to keep abreast with the latest innovation and practices in the field.
Conclusion
Subnet masks must be known about for internet enthusiasts. While it appears that way here, they are one of the fundamental components of how the internet operates optimally and effectively. The subnet mask is much like knowing one’s way through the various landmarks within your city; navigating through the cyber terrain.
If you’re ready to take charge of your network, see the following article. You can browse online subnet calculators or start working with IPv6 right now or take a networking class. Learning about subnet masks is not just the realm of IT specialists, it is exactly what makes you the master of the digital universe. Start now and enhance your Internet experience!