Updated in 2026
Technical vulnerabilities get patched. Software gets updated. But there is no patch for human trust. That is why social engineering continues to be one of the most effective and dangerous attack vectors in cybersecurity today.
A recent real-world incident shows how devastating these attacks can be, and why even organizations with strong technical controls remain vulnerable.
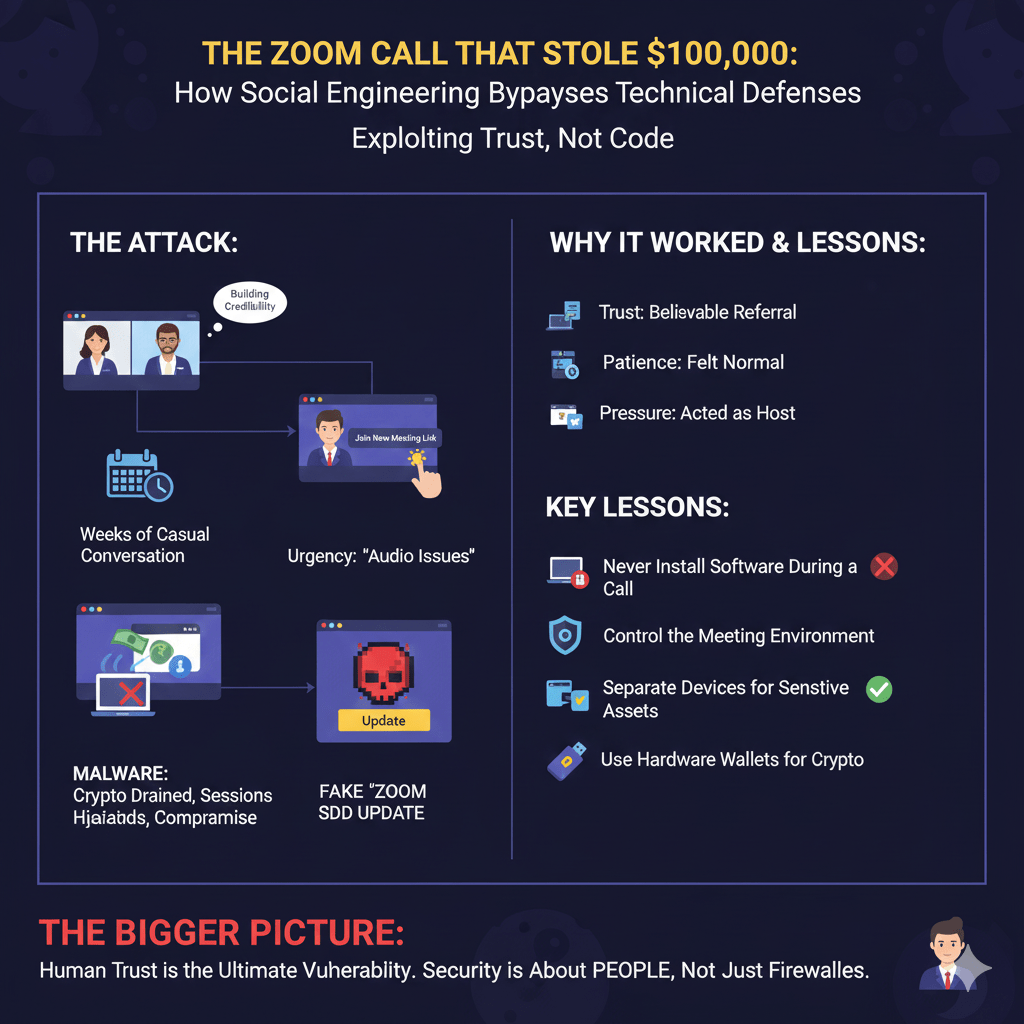
How the Attack Worked
The victim was invited to what appeared to be a legitimate partnership call. The attacker did not rush the process. Instead, they invested weeks building credibility through casual conversations, professional language, and a believable referral chain.
When the meeting started, nothing seemed out of place:
- Cameras were on
- Introductions were exchanged
- Light conversation filled the time while “others were joining”
Then came the pivot.
The attacker claimed to be experiencing VPN or audio issues and suggested switching to a different meeting link. When the victim clicked the new link, a prompt appeared asking them to “update the Zoom SDK” to enable audio or video.
The update was not legitimate software.
It was a disguised script. Once executed, it silently installed malware that:
- Drained cryptocurrency from hot wallets
- Hijacked active browser sessions and bypassed two-factor authentication
- Compromised connected accounts, including email and social media
Within moments, funds were moved, accounts were taken over, and the damage was irreversible.
Why It Worked
This attack did not exploit a flaw in Zoom or a missing software patch. It exploited human behavior.
- Trust: The attacker arrived through a referral and maintained consistent communication over time
- Patience: Nothing felt rushed or suspicious. The interaction mirrored normal business behavior
- Pressure: By presenting themselves as the meeting host with others waiting, the attacker created subtle urgency to comply quickly
The vulnerability was not technical. It was psychological.
Key Lessons Every Organization Should Learn
- Never install software during a live meeting
Legitimate platforms do not require third-party updates mid-call. Any prompt to install software during a meeting should be treated as a red flag.
- Control the meeting environment
If you host the meeting, stay on your platform. Do not switch links because of claimed connection issues.
- Separate devices for sensitive assets
Cryptocurrency wallets, financial systems, and administrative accounts should never be accessed from devices used for daily communications.
- Use hardware wallets for crypto assets
Hardware wallets require physical confirmation for transactions, which prevents automated theft even if a system is compromised.
- Expect the slow burn
Not all scams are rushed. The most effective social engineering attacks feel normal, professional, and unthreatening.
The Bigger Picture
Social engineering attacks like this highlight a critical reality: cybersecurity is not just about firewalls, antivirus tools, or patch management. It is about people.
Attackers are increasingly bypassing technical defenses by exploiting trust, routine, and human psychology. A smiling face on a video call can be more dangerous than a malicious file attachment.
This is why security awareness training, strict process controls, and a healthy level of skepticism are just as important as technical safeguards. The adversary is no longer always hidden in code. Sometimes, they are the person calmly speaking to you over video, waiting for you to click “Update.”