HIPAA exists because healthcare data is uniquely sensitive, highly distributed, and frequently accessed under pressure. Without enforceable safeguards, patient data would be exposed constantly through routine operations, not just cyberattacks.
HIPAA is not a cybersecurity framework. It is a risk management mandate that forces healthcare organizations to control how patient data is accessed, used, and protected across people, systems, and vendors.
At Mindcore Technologies, HIPAA failures almost never stem from a lack of intent. They stem from environments where access expanded faster than control.
What HIPAA Actually Is
HIPAA, the Health Insurance Portability and Accountability Act, is a U.S. federal law designed to protect the confidentiality, integrity, and availability of patient health information.
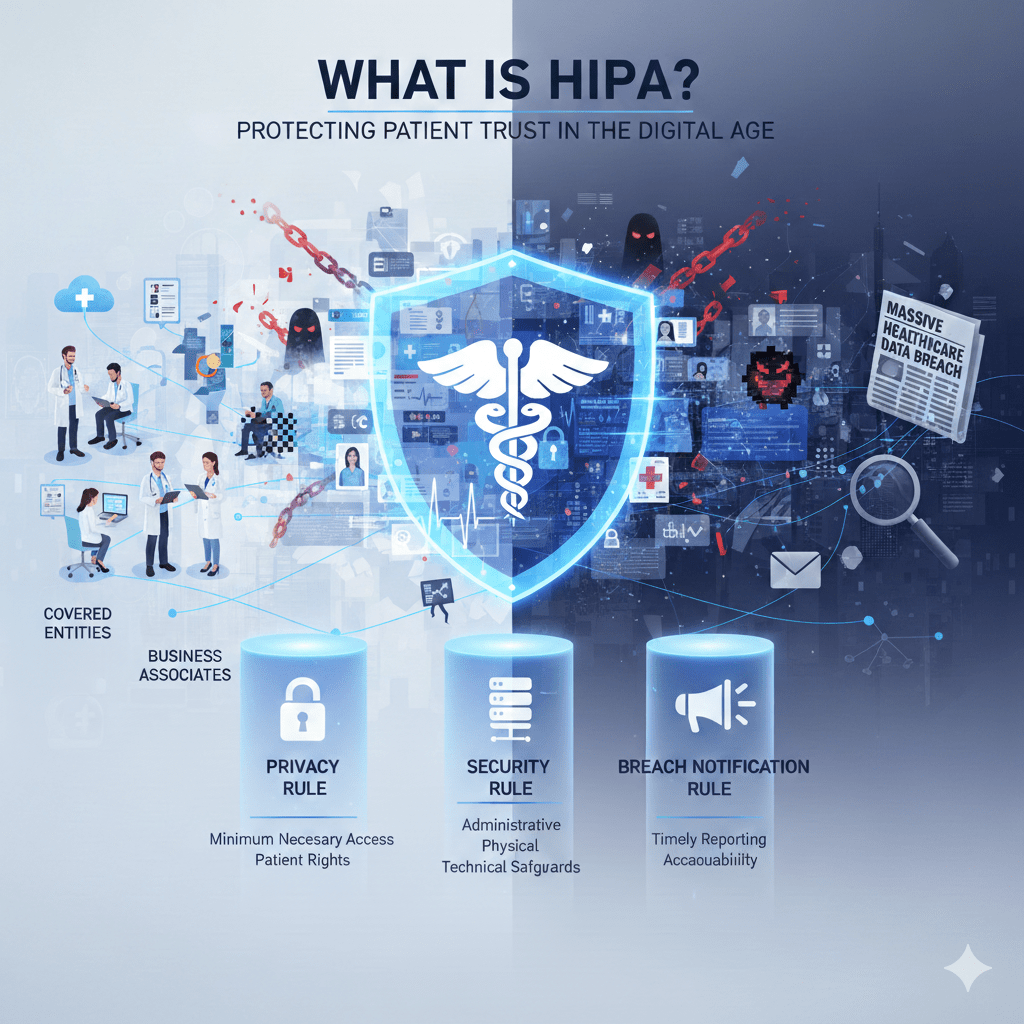
HIPAA applies to:
- Covered entities
Healthcare providers, health plans, and healthcare clearinghouses. - Business associates
Vendors and partners that handle protected health information, or PHI, on behalf of covered entities.
HIPAA sets expectations for how PHI must be handled, protected, and audited, regardless of whether it lives on paper, servers, or cloud platforms.
What HIPAA Is Designed to Protect
HIPAA focuses on Protected Health Information (PHI), which includes:
- Medical records and clinical notes
- Diagnoses, treatment details, and test results
- Billing and insurance information
- Patient identifiers such as names, addresses, and dates of birth
PHI becomes regulated when it can be linked to an individual. Once that link exists, HIPAA applies.
Why HIPAA Exists in the First Place
Healthcare data is different from other types of data.
HIPAA exists because:
- Healthcare requires frequent data access
Clinicians, administrators, and vendors all need timely access to PHI. - Care delivery cannot tolerate downtime
Availability matters as much as confidentiality. - Data is shared across many systems and partners
EHRs, billing platforms, labs, and third parties all touch PHI. - Patients cannot opt out of data collection
Trust is mandatory, not optional.
HIPAA forces organizations to manage these realities responsibly.
The Three Core HIPAA Rules That Matter Most
HIPAA is enforced primarily through three rules.
The Privacy Rule
The Privacy Rule governs who is allowed to access PHI and for what purpose.
It requires organizations to:
- Limit access to the minimum necessary
- Define permitted uses and disclosures
- Protect patient rights regarding their data
This rule focuses on intentional use, not technical controls.
The Security Rule
The Security Rule governs how electronic PHI (ePHI) is protected.
It requires safeguards across three areas:
- Administrative safeguards
Policies, risk assessments, and workforce training. - Physical safeguards
Facility access controls and device protection. - Technical safeguards
Access controls, audit logs, integrity protections, and transmission security.
This is where cybersecurity and IT architecture matter most.
The Breach Notification Rule
The Breach Notification Rule defines what must happen when PHI is exposed.
It requires:
- Timely notification to affected individuals
- Reporting to regulators
- Public disclosure for large breaches
This rule ensures accountability when controls fail.
Why HIPAA Is Still Challenging for Healthcare Organizations
HIPAA compliance is difficult because it is technology-agnostic but outcome-driven.
Common challenges include:
- Overly broad access to PHI
Users retain access far beyond their role. - Reliance on VPNs and legacy access models
Network trust creates unnecessary exposure. - Fragmented visibility across systems
Logs exist but are not correlated. - Third-party access that is poorly governed
Business associates often introduce risk. - Policies that are not enforced technically
Documentation exists, but architecture does not support it.
HIPAA failures usually reflect structural weaknesses, not negligence.
Why HIPAA Matters Beyond Avoiding Fines
HIPAA is often viewed as a compliance burden. That is a mistake.
HIPAA matters because it:
- Protects patient trust
Data mishandling erodes confidence in care providers. - Limits breach impact
Strong controls reduce exposure when incidents occur. - Reduces operational disruption
Ransomware and data loss affect patient care directly. - Aligns security with clinical reality
Access must be controlled without slowing care delivery.
Compliance is a side effect of good security architecture.
HIPAA and Modern Healthcare Technology
HIPAA applies regardless of how care is delivered.
This includes:
- Cloud-hosted EHR platforms
- Telehealth and virtual care systems
- Remote and hybrid clinical staff
- Third-party billing and analytics platforms
HIPAA does not prohibit cloud or remote access. It requires that risk is managed intentionally.
How Architecture Impacts HIPAA Compliance
HIPAA compliance improves dramatically when access models change.
Strong architectural controls include:
- Identity-based access instead of network trust
Access decisions follow users, not locations. - Least-privilege access by default
Users see only what they need. - Session-based access enforcement
Long-lived access is reduced. - Containment of PHI inside controlled environments
Data does not freely reach endpoints.
Architecture determines whether HIPAA controls are enforceable or aspirational.
How Mindcore Technologies Helps Organizations Meet HIPAA Expectations
Mindcore helps healthcare organizations align HIPAA requirements with real-world operations by:
- Assessing how PHI is actually accessed and used
Not how it is assumed to be used. - Reducing access sprawl through identity-driven controls
Least privilege is enforced consistently. - Limiting PHI exposure with secure workspace architectures
Data stays contained. - Improving audit visibility and evidence collection
Compliance becomes repeatable. - Addressing risk structurally, not cosmetically
Fixing root causes, not symptoms.
The goal is HIPAA compliance that supports care delivery, not hinders it.
A Simple HIPAA Reality Check
Your organization is at higher HIPAA risk if:
- Users have access to PHI beyond their role
- VPNs are required for EHR access
- PHI reaches unmanaged endpoints
- Audit evidence is assembled manually
- Business associate access is loosely controlled
These are architectural risks, not training failures.
Final Takeaway
HIPAA is not about checking boxes. It is about proving that patient data is accessed intentionally, protected consistently, and exposed only when necessary.
Healthcare organizations that treat HIPAA as an architectural discipline reduce risk, improve resilience, and maintain patient trust. Those that treat it as paperwork discover its importance only after something goes wrong.