(Updated in 2026)
If your organization treats data storage ethics as a compliance checkbox or a training slide item, you are exposing yourself to operational and reputational risk. Ethical data stewardship isn’t an abstract concept — it’s a tactical framework that governs how data is collected, accessed, stored, protected, and retained. Without concrete policies and resilient controls, even well-intended organizations can violate privacy, compromise sensitive systems, or fail to defend against evolving threats.
At Mindcore Technologies, we have presented on ethical data storage repeatedly because ethics must be engineered into systems and operations — not just discussed in theory.
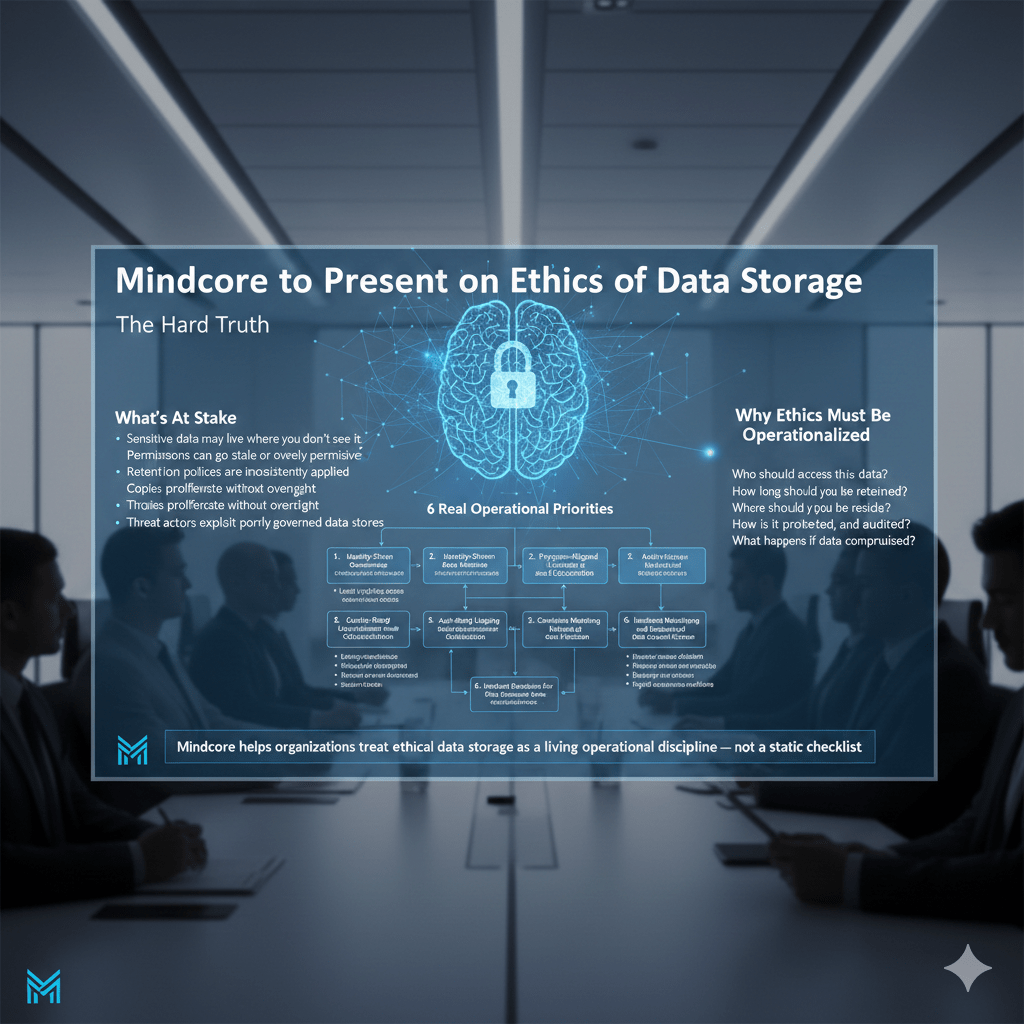
What’s At Stake
Today’s data environments are distributed, hybrid, and dynamic. Data sprawl crosses cloud services, remote endpoints, collaboration platforms, and integration interfaces. This complexity means:
- Sensitive data may live where you don’t see it
- Permissions can go stale or overly permissive
- Retention policies are inconsistently applied
- Copies proliferate without oversight
- Threat actors exploit poorly governed data stores
Ethical handling of data requires more than goodwill — it requires designed governance and enforceable controls.
Why Ethics Must Be Operationalized
Ethics without enforcement is a policy on paper. Security without clarity is a risk waiting to be exploited. Operational leaders must ask:
- Who should access this data?
- How long should it be retained?
- Where should it reside?
- How is it protected, monitored, and audited?
- What happens if data is compromised?
Answering these questions requires engineered systems, not slogans.
What We Are Presenting On — Real Operational Priorities
Mindcore’s presentation on the ethics of data storage isn’t a philosophical talk. It centers on defensible, practical control areas that must be engineered into every organization.
1. Identity-Driven Access Governance
Ethics begins with who can touch data — and why.
We implement:
- Least-privilege access
- Fine-grained role assignments
- Time-bound and context-based access
- Policy-enforced multi-factor authentication
Identity is not a gate — it is the security perimeter for ethical stewardship.
2. Purpose-Aligned Data Retention
Retaining data forever is not ethical unless there is purpose and compliance alignment.
We engineer:
- Retention policies tied to legal, business, and ethical requirements
- Automated lifecycle enforcement
- Data purge workflows with audit trails
Ethical storage means holding data only as long as it is justified and defensible.
3. Controlled Storage Locations and Classifications
Not all data should be stored in the same way.
We enforce:
- Data classification based on sensitivity
- Segregated storage with access boundaries
- Policy-enforced encryption at rest and in transit
- Cloud, hybrid, and on-premise controls tailored to risk
This ensures that sensitive data never travels or resides in low-trust zones.
4. Audit-Ready Logging and Evidence Collection
Ethics is backed by transparency.
We build logging that:
- Captures access events tied to identity
- Records changes and deletions
- Correlates data use with policy compliance
- Supplies evidence for internal and external review
Audit logs are not optional — they are defensible proof of ethical compliance.
5. Continuous Monitoring and Risk Detection
Static controls are not enough. Attackers exploit gaps between policy and practice.
We integrate:
- Behavior-based detection tied to data access
- Alerts on anomalous patterns
- Integration with SIEM and response orchestration
- Prioritized escalation with context
This ensures data ethics is operational — not passive.
6. Incident Readiness for Data Exposure Events
Ethics includes how you respond when something goes wrong.
We help teams build:
- Incident playbooks tailored to data exposure
- Rapid containment workflows
- Forensic evidence paths
- Communications with stakeholders
- Recovery paths aligned to business impact
Ethical stewardship requires responsiveness under pressure.
How Mindcore Technologies Embeds Ethics Into Practice
Data ethics isn’t a seminar — it’s part of how systems operate:
- Identity governance tied to access and retention
- Policy-enforced storage zones
- Automated retention and purge workflows
- Encrypted data paths with key management
- Continuous monitoring across systems
- Alerting with actionable risk signals
- Incident orchestration for exposure events
- Compliance evidence ready on demand
Mindcore helps organizations treat ethical data storage as a living operational discipline — not a static checklist.
What Your Team Should Do Next
If ethics is still “a policy document,” begin with these actions:
- Map sensitive data repositories and owners
- Define purpose and retention policies
- Enforce least-privilege identity models
- Classify and segment data by risk
- Integrate monitoring with alerts tied to policy violations
- Test incident response for ethical breach scenarios
- Capture audit evidence as part of normal operations
These steps transform ethics from concept to accountable action.
Final Thought
The ethics of data storage is not academic — it is operational, tactical, and defensible. As data environments grow in scale and complexity, organizations cannot rely on generic guidance. Ethical data stewardship must be engineered into systems, enforced by policies, and monitored continuously.
At Mindcore Technologies, we present and implement frameworks that drive ethical data storage into everyday operations — so organizations not only comply with expectations but defend them in practice.
This is how modern enterprises — including schools, healthcare providers, and regulated businesses — protect trust, data, and continuity.