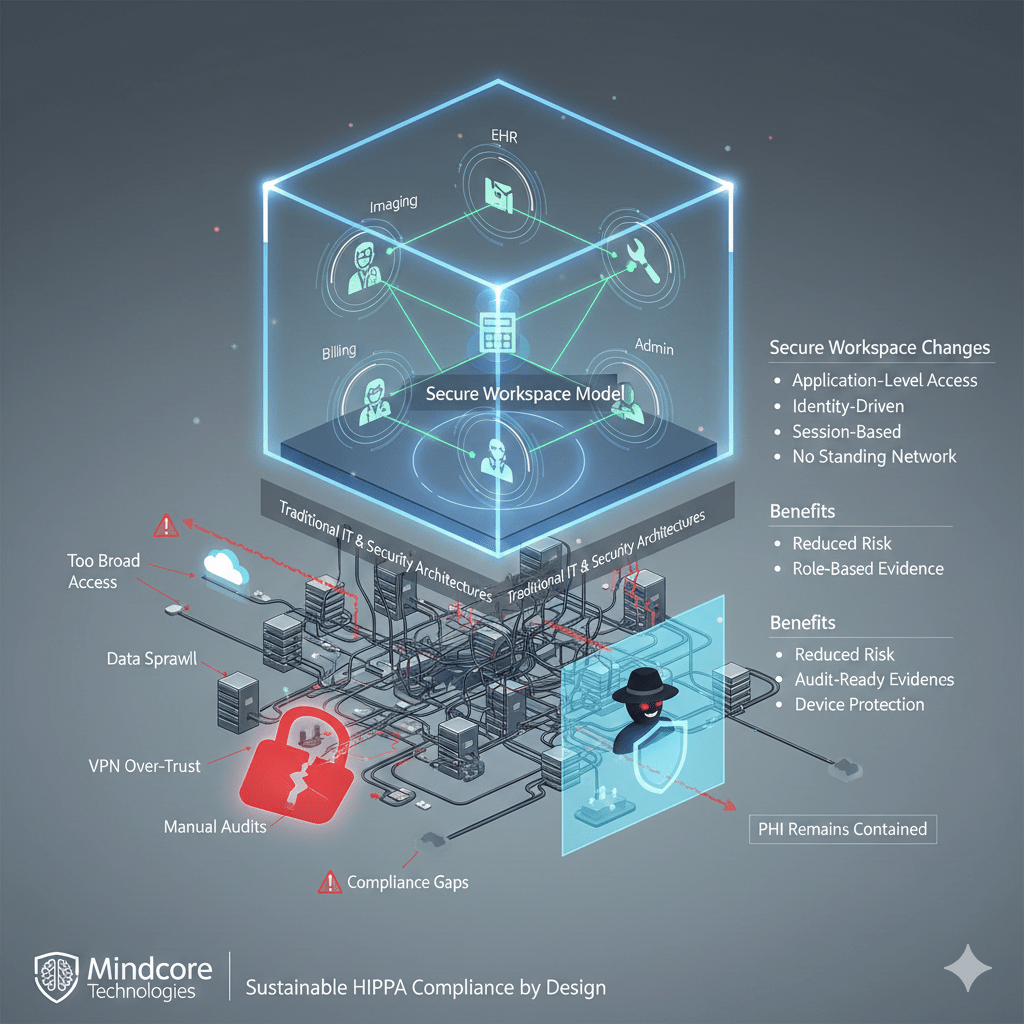
HIPAA compliance is not failing because healthcare organizations ignore the rules. It is failing because traditional IT and security architectures cannot consistently enforce what HIPAA actually requires in modern, cloud-based, remote-first environments.
Most compliance gaps are not malicious. They are structural.
At Mindcore Technologies, HIPAA-related findings, near misses, and breach investigations almost always trace back to the same issue: access is too broad, data is too reachable, and evidence is too difficult to produce under pressure. The secure workspace model exists to address these failures at the architectural level.
Why HIPAA Compliance Is So Difficult in Practice
HIPAA outlines clear expectations around safeguarding PHI, but healthcare environments make consistent enforcement difficult.
Common challenges include:
- Too many users with legitimate access
Clinicians, billing teams, administrators, contractors, and vendors all require access, making least-privilege enforcement complex and error-prone. - Remote and hybrid work as a permanent reality
PHI is accessed from home networks, personal devices, and shared environments that were never designed for healthcare-grade security. - VPN-based access models that overextend trust
Once connected, users often inherit network-level access that far exceeds what HIPAA’s minimum necessary standard allows. - Data sprawl across platforms
EHRs, document management systems, imaging platforms, and SaaS tools duplicate PHI across multiple locations. - Audit evidence that is fragmented and manual
Proving who accessed what and when often requires pulling logs from multiple systems under time pressure.
These challenges create compliance risk even when teams are well-intentioned.
The Gap Between HIPAA Requirements and Traditional Security
HIPAA expects organizations to demonstrate:
- Controlled access to PHI
- Enforcement of least privilege
- Protection against unauthorized access
- Clear audit trails and accountability
- Risk reduction, not just policy intent
Traditional security tools focus on protecting networks, not governing PHI access. This gap is where most compliance failures occur.
Why VPN-Centric Models Struggle With HIPAA
VPNs conflict with HIPAA requirements in subtle but serious ways:
- They grant network access, not data-specific access
Users often gain visibility into systems and resources beyond their role. - Sessions persist longer than necessary
Standing access increases the risk of misuse and session hijacking. - Access paths are difficult to audit at the application level
Logs show that a user connected, not what PHI they accessed. - Endpoints become part of the trusted environment
PHI becomes reachable from devices that are difficult to fully control.
From a HIPAA perspective, VPNs make “minimum necessary” enforcement extremely difficult.
What the Secure Workspace Model Changes
The secure workspace model shifts HIPAA compliance from policy enforcement to architectural enforcement.
Instead of extending trust outward, it:
- Contains PHI inside a controlled workspace
Data lives in a secure environment rather than on endpoints. - Delivers access at the application level
Users interact only with approved systems, not networks or file shares. - Enforces identity-driven, session-based access
Access is continuously verified and scoped to purpose. - Eliminates standing network connectivity
Network paths exist only for the duration of an approved session.
This aligns directly with HIPAA’s minimum necessary standard.
How Secure Workspaces Address Core HIPAA Challenges
Minimum Necessary Access
- Role-based access is enforced by design
Clinicians, billing staff, and administrators see only what their role requires. - No inherited network visibility
Users cannot explore or stumble into systems containing unrelated PHI. - Access expires automatically
Standing access does not accumulate over time.
This reduces both accidental and intentional overexposure.
PHI Protection Across Devices
- PHI remains inside the workspace
Data is not stored, cached, or synced to local devices. - Reduced risk from lost or compromised endpoints
Devices become access terminals, not data repositories. - Controlled data movement
Copying, exporting, or transferring PHI is restricted and observable.
This dramatically lowers breach impact.
Auditability and Evidence Readiness
- Application-level audit trails
Logs show exactly which systems were accessed and when. - Session visibility
Duration, behavior, and access patterns are centrally recorded. - Simplified evidence collection
Audits rely on structured logs, not screenshots or assumptions.
Compliance becomes defensible under scrutiny.
Vendor and Third-Party Access Control
- Access is tightly scoped and time-bound
Vendors receive only the access they need, only when they need it. - No network-level trust
Third parties never join the internal network. - Immediate revocation without disruption
Access can be removed instantly without password resets or firewall changes.
This closes one of healthcare’s most common compliance gaps.
Why Secure Workspaces Reduce Breach and Compliance Risk Together
HIPAA compliance and breach prevention are not separate problems.
Secure workspaces:
- Reduce how much PHI is reachable
- Limit the blast radius of compromised credentials
- Improve detection of abnormal access
- Make compliance evidence readily available
Security and compliance reinforce each other instead of competing.
How Mindcore Technologies Implements Secure Workspaces for HIPAA
Mindcore deploys secure workspace architectures for healthcare organizations by:
- Mapping PHI access to real workflows
Security reflects clinical and administrative reality. - Defining role-based access aligned to HIPAA standards
Minimum necessary access is enforced technically. - Replacing VPN-based access models
Network exposure is removed from PHI access entirely. - Enforcing device and session controls
Access adapts dynamically based on risk. - Providing centralized visibility and governance
Security, IT, and compliance teams share a single source of truth.
The goal is not theoretical compliance. It is operational confidence.
A Simple HIPAA Reality Check
Your organization faces elevated HIPAA risk if:
- VPNs are still required for PHI access
- Users can access systems beyond their role
- PHI reaches unmanaged endpoints
- Audit evidence requires manual reconstruction
- Access reviews are infrequent or informal
These are architectural risks, not training issues.
Final Takeaway
HIPAA compliance is becoming harder not because requirements are unreasonable, but because traditional access models cannot enforce them consistently. Secure workspaces close this gap by containing PHI, enforcing minimum necessary access, and producing audit-ready evidence by design.
For healthcare organizations under constant regulatory and ransomware pressure, the secure workspace model is no longer an optional enhancement. It is the most practical path to sustainable HIPAA compliance.