Your Central Command for Preemptive Cyber Defense.
Compliance Ready
Mindcore Secure Workspace Solutions Powered by
Tehama Technology
Stop threats before they strike. ShieldHQ combines secure cloud workspaces, zero-trust access, and compliance automation with an invisible data-in-motion layer to deliver an AI-fortified, quantum-resilient environment. It is the ultimate defense for healthcare and enterprise leaders demanding impenetrable protection and total compliance.
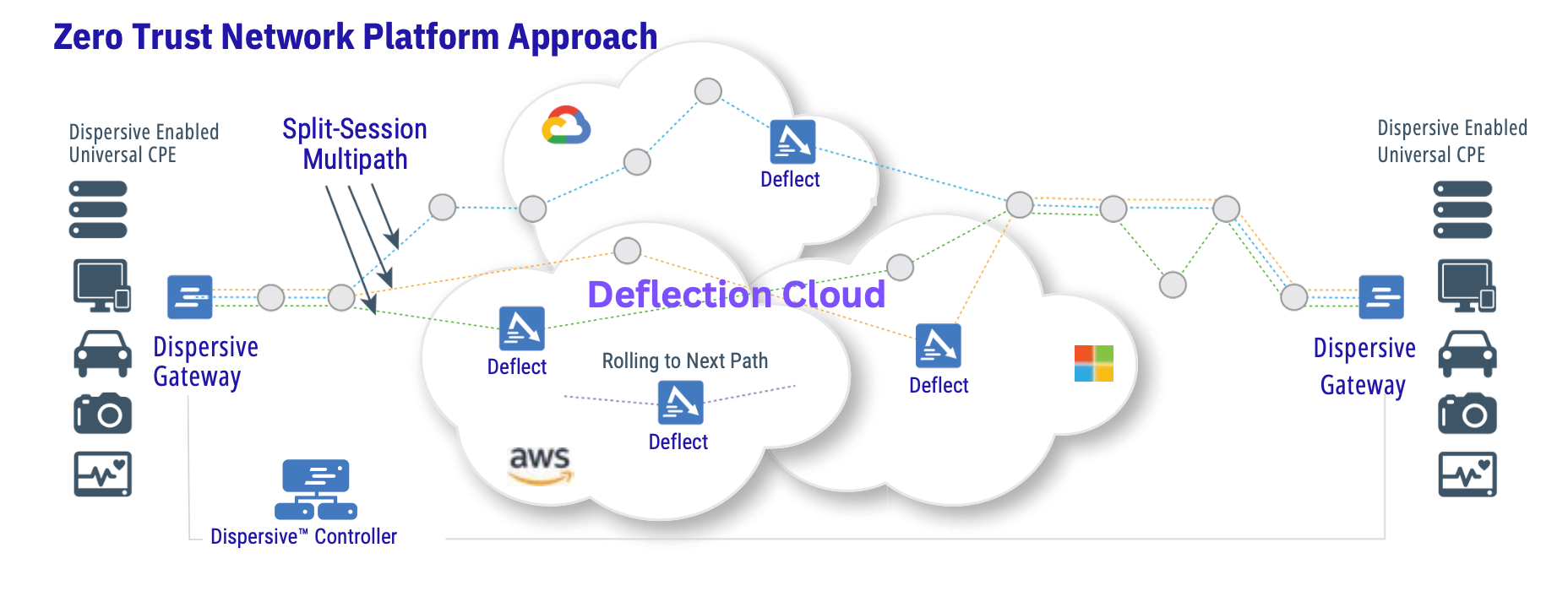
Powered by Dispersive® Stealth Networking.
Your Unfair Competitive Advantage
The digital world is a war zone. The status quo is burning cash on reactive defenses—fighting fires and praying you aren’t the next target.
Mindcore’s ShieldHQ changes the game. We don’t just secure your data; we remove it from the battlefield.
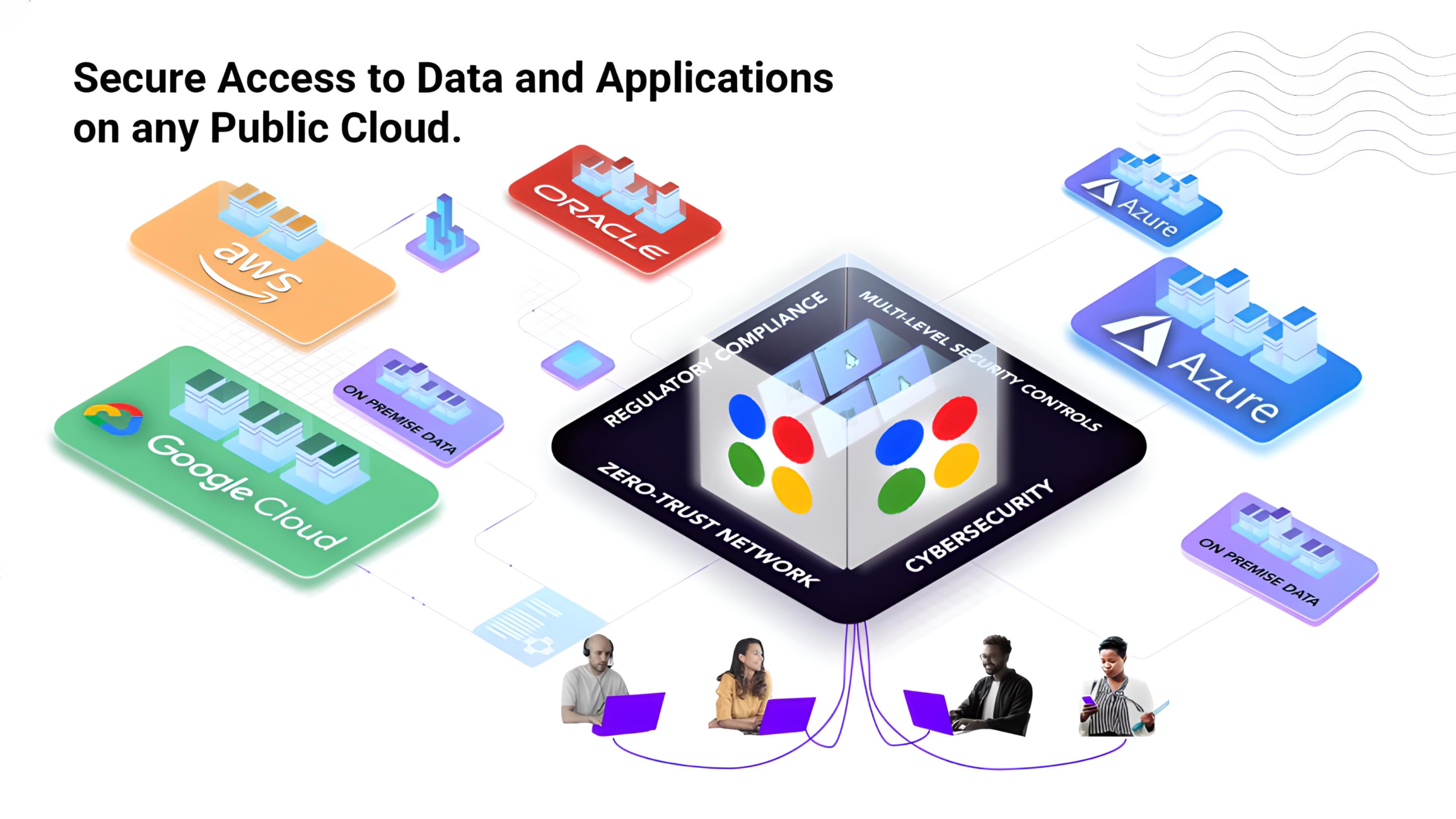
By integrating Mindcore’s security and compliance platform with Dispersive® Stealth Networking, ShieldHQ creates a business environment that is:
- Invisible to Attackers: Enabled by Dispersive® Stealth Networking, network paths and traffic are hidden from discovery, eliminating exposed attack surfaces.
- Quantum-Ready: Built on crypto-agile, quantum-resilient data-in-motion protections designed to evolve as new threats emerge.
- Hyper-Efficient: Delivering 10x network speeds while slashing IT overhead.
This isn’t just “cybersecurity.” This is Operational Supremacy.
ShieldHQ — Compliance Without Compromise
Secure your entire organization with an AI-powered, compliance-ready environment featuring built-in audit trails and zero-trust access
- 30–50% lower IT costs
- 90% fewer security incidents
- 20–35% less security spend
- 90% faster deployment
- Zero data loss or endpoint risk
- 100% audit visibility
- 24/7 AI threat monitoring

- HIPAA / HITRUST
- SOC 2 Type 2
- NIST 2.0 / CMMC
- GDPR / PCI-DSS
- FINRA / SEC / SOX
- Zero Trust Architecture
- AI Governance
- Automated Policies
- Unified Compliance
- Instant Vendor Access
- No VPNs or Hardware
ROI That Demands Attention
Stop viewing security as a cost center. ShieldHQ turns your infrastructure into a value driver.

Organizations deploying ShieldHQ, powered by Dispersive® Stealth Networking, and Mindcore’s automation and governance model see a massive ROI with a payback period of just ~10 months.
We automate the mundane. We reduce the 5-Year TCO from $12.7M (manual) to $1.78M—a $9.1M net savings.
With the average breach costing millions, ShieldHQ eliminates the attack surface entirely.

Whether it’s HIPAA, SOC 2, or NIST 2.0, ShieldHQ creates a compliance-ready state out of the box, saving hundreds of hours in audit prep.
The Fortress & The Cloak
ShieldHQ replaces the “Castle and Moat” with a moving target that adversaries cannot hit.
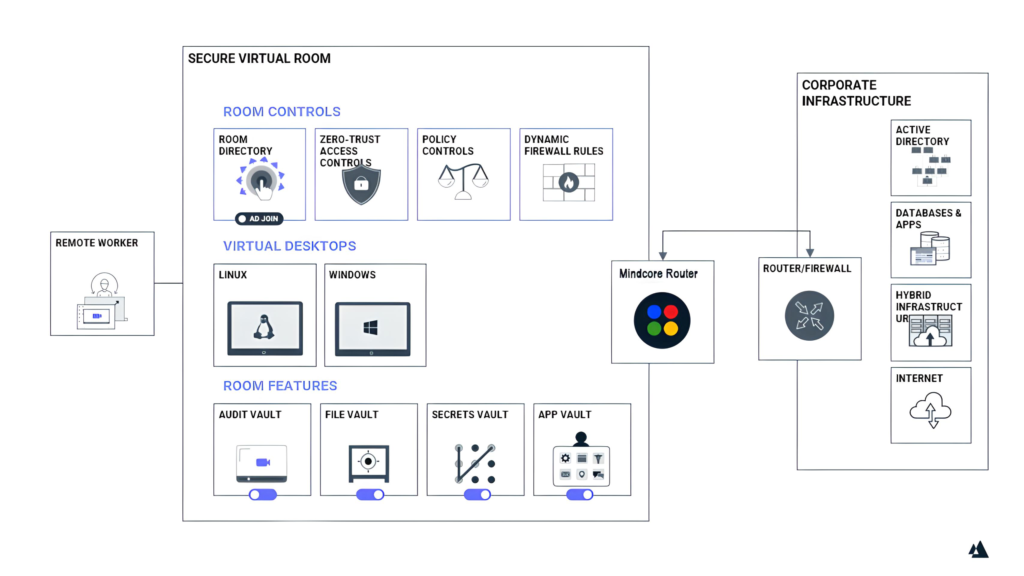
Your sensitive operations move into a Secure Cloud Workspace. Data never touches the endpoint device. Your team works in a high-performance, isolated environment where data exfiltration is mathematically impossible.
The Result: Zero Endpoint Risk. Zero Ransomware Spread.
We don’t just encrypt the pipe; we hide it. Using Dispersive® Stealth Networking’s multipath dispersion, ShieldHQ fragments, encrypts, and scatters data across multiple independent paths..
The Result: To the outside world, your digital footprint simply vanishes. No VPNs. No open ports. No targets.
While others react to attacks, ShieldHQ orchestrates preemptive cyber defense policies across secure enclaves and the underlying Dispersive® Stealth Networking layer, enabling continuous movement of keys, paths, and access states.
Data Sovereignty: Total Lifecycle Protection
Mindcore’s data protection capabilities ensure sensitive information remains secure through its entire lifecycle—whether at rest, in transit, or in use.

Discovery & Classification: AI-driven identification of sensitive assets.
Rights Management: Strict control over data usage and sharing.
Activity Monitoring: Granular tracking of every interaction.
DLP: Zero-trust prevention of unauthorized exfiltration19.

Data-in-motion cryptographic protections are provided by Dispersive® Stealth Networking, while ShieldHQ governs policy enforcement, access controls, and compliance reporting.
In-Transit Encryption: Military-grade protection for moving data.
At-Rest Encryption: Securing stored information.
Automated Key Rotation: Eliminating the risk of static keys.
Certificate Management: Streamlined, automated security certificates.

AI Isolation: Separate AI workloads from sensitive core environments.
Model Governance: Control how AI systems ingest and process data.
Full Audit Trails: Complete visibility into AI operations and prompts.
The Gap is Widening. Don’t Be Left Exposed.
There are two types of companies emerging in 2026
- The Vulnerable: Still using static VPNs, managing certificates on spreadsheets, and praying their firewall holds.
- The Shielded: Operating on ShieldHQ, powered by Dispersive® Stealth Networking. Invisible to ransomware, 10x faster, automated compliance, and an IT budget focused on innovation, not repair.
You have the opportunity to secure the ultimate competitive edge.
Frequently Asked Questions
ShieldHQ is an enterprise-grade secure workspace and cyber defense platform designed to protect sensitive data by eliminating traditional network attack surfaces. It combines Zero Trust architecture, stealth networking, and isolated secure enclaves to keep systems invisible and inaccessible to attackers.
ShieldHQ enforces secure access, encrypted sessions, audit visibility, and data isolation by design. This reduces compliance risk and simplifies requirements for frameworks such as HIPAA, SOC 2, NIST, PCI-DSS, and other regulatory standards.
ShieldHQ can be deployed rapidly without major infrastructure changes. Organizations can onboard users, vendors, and teams quickly while immediately improving security posture, visibility, and compliance readiness.
Unlike VPNs that rely on static tunnels and exposed gateways, ShieldHQ removes network visibility entirely. Traffic is dynamically protected and isolated, preventing interception, lateral movement, and credential-based attacks that commonly bypass VPN security.
ShieldHQ is designed for organizations handling sensitive or regulated data, including healthcare, financial services, legal, and enterprise environments that require secure remote access, vendor control, and strong audit readiness.