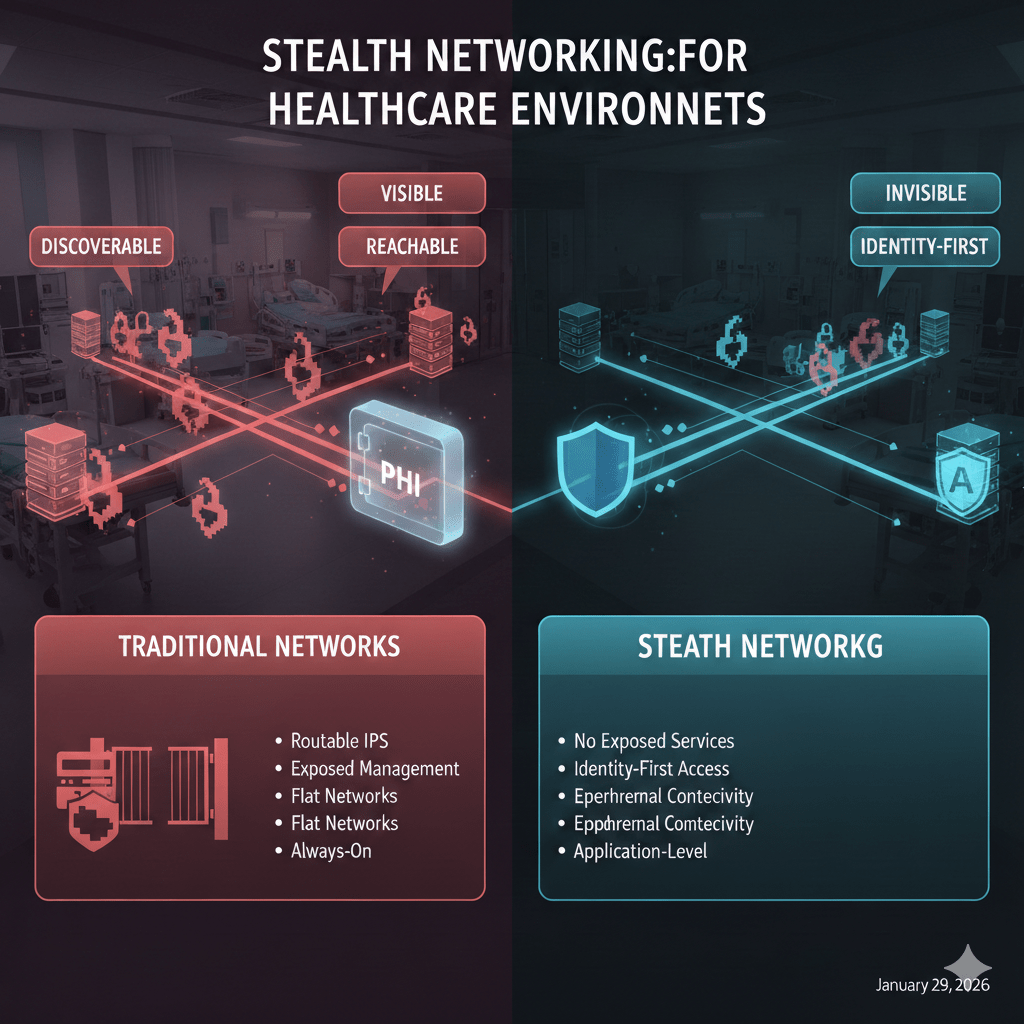
Healthcare networks are exposed long before an attacker ever authenticates. The problem is not weak passwords or missing tools. The problem is that most healthcare infrastructure is visible, discoverable, and reachable by design.
If attackers can see it, they can target it.
At Mindcore Technologies, breach investigations repeatedly show that attackers don’t need to break in. They map exposed services, identify reachable systems, and wait for one access failure to cascade. Stealth networking exists to remove that visibility entirely.
What Stealth Networking Actually Means
Stealth networking is not obfuscation and it is not security through obscurity. It is an architectural approach where systems are deliberately hidden from discovery unless identity, context, and authorization are proven first.
In practical terms, stealth networking ensures:
- Systems do not respond to unsolicited traffic
- Infrastructure does not appear in scans
- Applications are invisible to unauthorized users
- Network paths do not exist until access is validated
If you cannot see it, you cannot attack it.
Why Traditional Healthcare Networks Are Easy to Target
Most healthcare environments still operate with:
- Routable IP-based infrastructure
Servers, applications, and devices are reachable across internal and external networks, making them discoverable through scanning. - Exposed management planes
RDP, SSH, VPN gateways, and web consoles often remain visible even when secured with credentials. - Flat or lightly segmented networks
Once attackers gain a foothold, lateral movement becomes trivial. - Always-on network presence
Systems advertise themselves continuously, increasing attack surface 24/7.
Security tools try to defend what is already exposed. Stealth networking removes the exposure.
Why Healthcare Is a Prime Candidate for Stealth Networking
Healthcare environments have unique risk factors:
- High-value data (PHI)
Patient data commands premium prices and carries regulatory penalties. - Low tolerance for downtime
Clinical operations cannot afford disruptive security controls. - Complex vendor ecosystems
Medical devices, billing partners, and SaaS platforms increase entry points. - Regulatory pressure (HIPAA)
Access must be provable, controlled, and auditable.
Stealth networking aligns security with these constraints by reducing attack surface without disrupting workflows.
How Stealth Networking Works in Practice
Stealth networking changes the access model entirely:
- No exposed services
Applications and systems do not listen for inbound connections from unauthorized users. - Identity-first access
Users authenticate before network paths are created. - Ephemeral connectivity
Network connections exist only for the duration of an approved session. - Application-level exposure
Users access specific applications, not networks or subnets.
Attackers scanning the environment see nothing to exploit.
Stealth Networking vs Traditional Network Security
Traditional security focuses on:
- Firewalls
- IDS/IPS
- VPNs
- Network segmentation
Stealth networking focuses on:
- Removing discoverability
- Eliminating standing network access
- Hiding infrastructure entirely
Firewalls protect visible assets. Stealth networking removes them from view.
Why VPNs Undermine Stealth in Healthcare
VPNs directly conflict with stealth principles:
- They advertise an entry point
VPN gateways are visible and constantly targeted. - They extend the network to endpoints
Once connected, devices gain broad visibility. - They rely on static credentials and sessions
Compromised credentials provide reusable access. - They complicate audit trails
Activity happens inside the network, not at the application layer.
Stealth networking eliminates the need for VPNs altogether.
How Stealth Networking Limits Ransomware and Lateral Movement
When stealth networking is implemented correctly:
- Attackers cannot scan for targets
Systems do not respond to probes or enumeration. - Initial access does not reveal the environment
Even compromised credentials expose only approved applications. - Lateral movement is blocked by design
There are no network paths to pivot across. - Blast radius is minimized
Compromise is contained to a single session or application.
This directly reduces ransomware propagation and dwell time.
Stealth Networking and HIPAA Compliance
HIPAA requires:
- Controlled access to PHI
- Least privilege enforcement
- Clear audit trails
- Reduced exposure risk
Stealth networking supports these requirements by:
- Limiting who can even see systems containing PHI
- Restricting access at the application level
- Recording every session and interaction
- Reducing unnecessary network exposure
Compliance becomes an architectural outcome, not a documentation exercise.
Where Stealth Networking Fits in Modern Healthcare Security
Stealth networking works best when combined with:
- Zero-trust identity models
- Secure workspace architectures
- Strong device posture enforcement
- Centralized logging and monitoring
It does not replace security controls. It removes the need to defend exposed infrastructure.
How ShieldHQ Applies Stealth Networking in Healthcare
ShieldHQ operationalizes stealth networking by:
- Making applications invisible until identity is verified
Unauthorized users cannot discover systems at all. - Creating session-based, ephemeral access paths
Network connectivity exists only when explicitly approved. - Keeping PHI inside a controlled workspace
Data never reaches unmanaged endpoints. - Eliminating VPNs and exposed gateways
Attack entry points are removed, not hardened. - Providing centralized visibility and audit logs
Every session is observable and reviewable.
This is stealth networking implemented in a way healthcare teams can actually operate.
Common Misconceptions About Stealth Networking
- “It’s just hiding IPs”
Stealth networking removes reachability, not just visibility. - “It’s too complex for healthcare”
It simplifies environments by removing VPNs and flat networks. - “It replaces security tools”
It reduces exposure so security tools have less to defend.
A Simple Healthcare Reality Check
Your environment is not stealthy if:
- VPN gateways are publicly reachable
- Servers respond to scans
- Internal IP ranges are visible after login
- Lateral movement is possible
- Network access persists indefinitely
These are structural risks, not configuration issues.
Final Takeaway
Stealth networking represents a fundamental shift in how healthcare environments are protected. Instead of defending visible infrastructure, it removes that infrastructure from view entirely. For healthcare organizations facing ransomware, compliance pressure, and expanding attack surfaces, this approach dramatically reduces risk without disrupting care delivery.
Stealth networking is not an advanced add-on. It is becoming a baseline requirement for healthcare environments that need security without downtime.