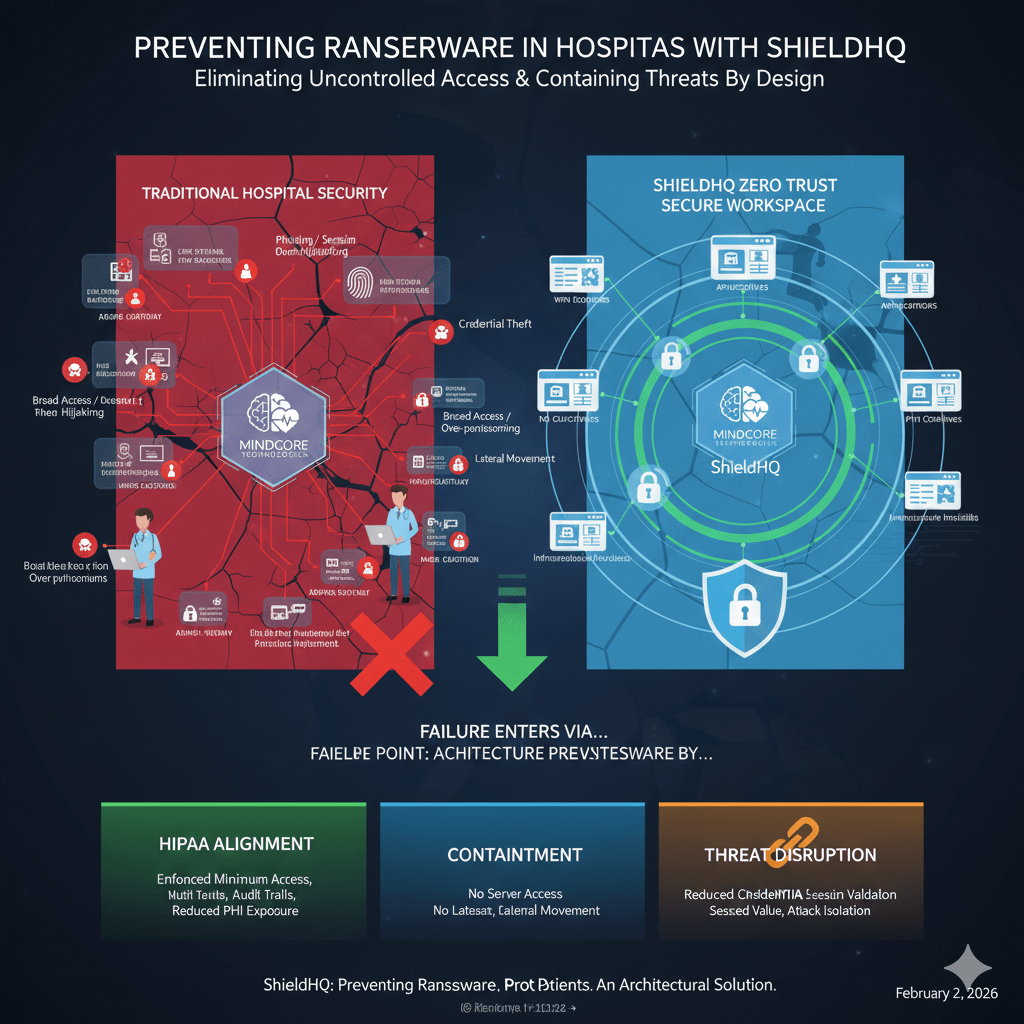
Hospital ransomware does not begin with encryption. It begins with uncontrolled access, excessive visibility, and trust that lasts too long. By the time systems lock up, attackers have already mapped the environment, moved laterally, and identified the most operationally critical systems.
That is the failure point ShieldHQ is designed to remove.
At Mindcore Technologies, hospital incident reviews show the same pattern repeatedly: attackers did not bypass defenses, they used the access hospitals already granted. ShieldHQ prevents ransomware by redesigning access so compromise cannot escalate.
Why Hospitals Are Prime Ransomware Targets
Hospitals combine high-value data with low tolerance for downtime.
Attackers focus on hospitals because:
- Clinical downtime has immediate patient impact
Even short outages disrupt care delivery, making ransom pressure highly effective. - EHRs and clinical systems contain regulated PHI
Data extortion adds leverage beyond encryption alone. - Access is broad across many roles
Clinicians, nurses, admins, billing teams, vendors, and IT all require access, increasing over-permissioning risk. - Legacy access models still dominate
VPNs and flat networks allow compromise to spread quickly once credentials are stolen.
Ransomware succeeds because hospitals prioritize availability over containment.
How Ransomware Actually Enters Hospital Environments
Contrary to common belief, most ransomware does not enter through exploits.
It enters through:
- Credential theft via infostealers
Malware harvests usernames, passwords, and browser sessions from compromised endpoints. - Phishing and session hijacking
Attackers steal authenticated sessions rather than credentials, bypassing MFA entirely. - VPN reuse and standing access
Stolen credentials provide repeatable, trusted network access. - Excessive permissions that were never reviewed
One compromised account often exposes far more systems than intended.
From a monitoring standpoint, activity appears legitimate until encryption begins.
Why Traditional Hospital Defenses Fail Against Ransomware
Hospitals often rely on:
- Perimeter security and endpoint tools
These detect malware but do not prevent credential misuse. - VPN-based remote access
VPNs collapse identity compromise into broad network access. - Flat or lightly segmented networks
Once inside, ransomware spreads rapidly. - Reactive response models
Teams respond after damage, not before escalation.
These controls assume attackers break in. Modern attackers log in.
How ShieldHQ Prevents Ransomware Architecturally
ShieldHQ prevents ransomware by removing the conditions it depends on.
Eliminating Network Exposure
- No VPNs or exposed gateways
Attackers lose a primary entry point entirely. - Applications are not routable or discoverable
Systems do not respond to scans or probes. - Infrastructure remains invisible until identity is verified
Attackers cannot map targets before access is granted.
Without visibility, ransomware cannot stage attacks.
Containing Access with Secure Workspaces
- Application-level access only
Users interact with specific systems, not networks or servers. - No lateral movement paths
Compromise is confined to a single application session. - Ephemeral, session-based connectivity
Access exists only while approved and active.
This containment prevents ransomware from spreading.
Protecting PHI by Design
- PHI remains inside the secure workspace
Data does not reach endpoints where ransomware operates. - No access to file systems or databases directly
Ransomware cannot encrypt what it cannot reach. - Controlled data movement
Exfiltration paths are restricted and observable.
This reduces both encryption and extortion risk.
Stopping Common Hospital Ransomware Scenarios
Stolen Credentials
- Credentials alone do not provide network access
- Sessions are tightly scoped and monitored
- Access expires automatically
Stolen credentials lose their operational value.
Phishing-Based Session Theft
- Sessions are continuously evaluated
- Abnormal behavior triggers revocation
- Long-lived sessions are eliminated
Attackers cannot persist silently.
Lateral Ransomware Spread
- No flat networks to traverse
- No server-level access
- No system discovery
Ransomware stalls at the first system.
Why ShieldHQ Improves Ransomware Resilience Without Downtime
Hospitals cannot afford security that disrupts care.
ShieldHQ supports operational continuity by:
- Maintaining consistent application availability
Security changes do not interrupt clinical workflows. - Reducing dependency on fragile network paths
Fewer moving parts mean fewer failures. - Simplifying access for clinicians and vendors
Secure access without VPN friction improves reliability.
Security becomes invisible to patient care.
Ransomware Prevention and HIPAA Alignment
HIPAA expects organizations to reduce risk, not just respond to incidents.
ShieldHQ supports this by:
- Enforcing minimum necessary access
Users cannot reach systems beyond their role. - Reducing PHI exposure footprint
Data is accessible only through controlled workspaces. - Providing detailed audit trails
Access to PHI is fully observable and reviewable. - Limiting breach blast radius
Even successful compromise has minimal impact.
Ransomware prevention and compliance reinforce each other.
How Mindcore Technologies Deploys ShieldHQ in Hospitals
Mindcore implements ShieldHQ for hospitals by:
- Mapping clinical, administrative, and vendor workflows
Access models reflect real operational needs. - Replacing VPN-based access paths
Network exposure is removed entirely. - Defining role-based access to EHR and clinical systems
Permissions align with responsibility, not convenience. - Enforcing device and session posture controls
Access adapts dynamically to risk. - Providing centralized visibility and governance
Security teams maintain continuous oversight.
The result is ransomware prevention without operational disruption.
A Simple Hospital Ransomware Risk Check
Your hospital remains vulnerable if:
- VPN access is still required
- Sessions persist indefinitely
- Users can access systems they do not need
- PHI reaches unmanaged endpoints
- Ransomware response is reactive
These are architectural risks, not training gaps.
Final Takeaway
Preventing ransomware in hospitals requires more than detection and backups. It requires removing visibility, eliminating lateral movement, and containing access by design. ShieldHQ achieves this by replacing trust-based access with zero trust secure workspaces that prevent ransomware from spreading in the first place.
For hospitals facing constant ransomware pressure, ShieldHQ is not an additional control. It is the architecture that makes prevention possible.