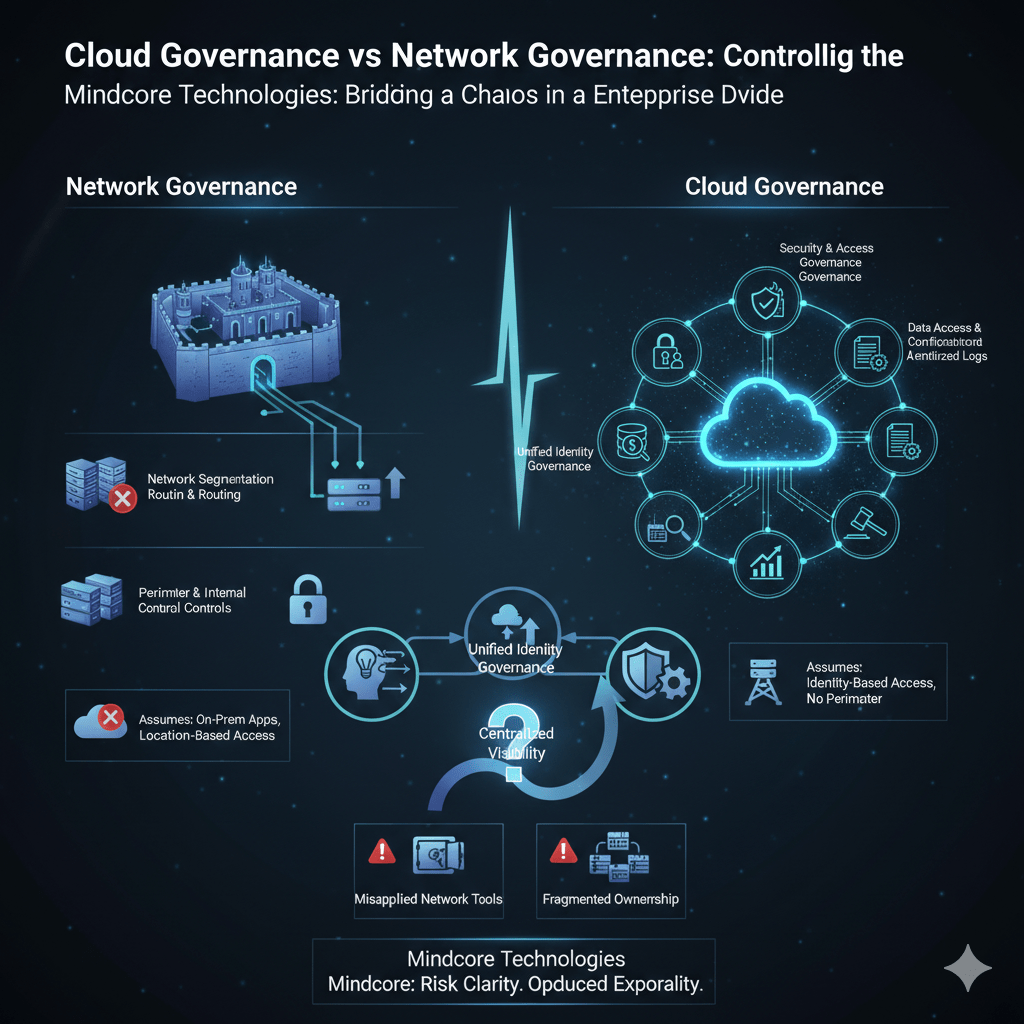
Most organizations struggle with governance because they are trying to apply network-era control models to cloud-era environments. Cloud governance and network governance solve different problems, operate on different assumptions, and fail in different ways when misapplied.
Understanding the distinction is not academic. It directly affects security exposure, audit outcomes, and operational stability.
At Mindcore Technologies, governance failures almost always trace back to confusing these two disciplines or assuming one replaces the other.
What Network Governance Is Designed to Control
Network governance is the discipline of controlling connectivity, traffic flow, and trust inside a network boundary.
It focuses on:
- Network segmentation and routing
Defining which systems can communicate and how traffic flows between them. - Perimeter and internal controls
Firewalls, VLANs, ACLs, and intrusion prevention that regulate network paths. - Device-level trust assumptions
Systems inside the network are often treated as more trusted than those outside. - Traffic visibility and inspection
Monitoring packets, flows, and anomalies moving across the network.
Network governance assumes that control begins at the network layer.
Why Network Governance Worked Historically
Network governance was effective when:
- Applications lived inside data centers
- Users worked primarily on-prem
- Access was granted by location
- Data rarely left the internal network
In that model, controlling the network effectively controlled access to systems and data.
That assumption no longer holds.
What Cloud Governance Is Designed to Control
Cloud governance is the discipline of controlling how cloud services, identities, data, and resources are used once network boundaries disappear.
It focuses on:
- Identity and access governance
Who can access cloud services, what actions they can perform, and under what conditions. - Resource creation and configuration
How cloud resources are deployed, configured, and secured at scale. - Data access and movement
How sensitive data is classified, shared, exported, and audited across platforms. - Cost and usage accountability
Who is consuming cloud resources and why.
Cloud governance assumes identity, not network location, is the primary control plane.
Why Cloud Governance Became Necessary
Cloud breaks the assumptions network governance relies on:
- Users authenticate directly to cloud services
Network controls are bypassed entirely. - Applications are internet-facing by design
There is no meaningful internal perimeter. - Data lives across SaaS, IaaS, and integrations
Ownership and visibility fragment quickly. - Teams can deploy resources instantly
Centralized network approval no longer gates activity.
Cloud governance exists because the network no longer defines control.
The Core Difference in One Sentence
- Network governance controls how systems communicate
- Cloud governance controls how identities, data, and services are used
Both matter, but they solve different problems.
Where Organizations Get This Wrong
The most common mistakes include:
- Trying to enforce cloud governance with network tools
Firewalls cannot control SaaS permissions or data sharing. - Assuming zero trust networking replaces cloud governance
Zero trust reduces network trust, but does not manage cloud identities, data, or spend. - Ignoring network governance after cloud adoption
Hybrid environments still rely on networks for internal systems. - Fragmenting governance ownership
Network teams govern networks, cloud teams govern cloud, but no one governs the whole picture.
This creates blind spots attackers exploit.
How Cloud and Network Governance Must Work Together
Modern environments require layered governance, not substitution.
Effective alignment looks like:
- Network governance limits lateral movement
Segmentation and isolation reduce blast radius after access is gained. - Cloud governance limits access and exposure
Identity, permissions, and data controls prevent overreach. - Identity governance spans both domains
Access decisions follow users, not locations. - Visibility is centralized across layers
Activity is correlated across network and cloud services.
One without the other creates false confidence.
Governance Failures We See in the Wild
In real environments, failures look like:
- Strong network segmentation but excessive SaaS permissions
- Locked-down firewalls but unrestricted data sharing
- Well-governed cloud identities with flat internal networks
- Compliance controls that exist on paper but not in architecture
Governance gaps almost always exist between layers, not within them.
How Secure Workspaces Bridge the Gap
Secure workspace architectures help unify governance by:
- Removing network trust from access decisions
Users do not join internal networks to access services. - Enforcing application-level access
Network paths are irrelevant to data access. - Reducing dependency on endpoint and location trust
Identity and session context become primary controls. - Centralizing access visibility
Activity is tracked consistently regardless of location.
This reduces the friction between network and cloud governance models.
How Mindcore Technologies Approaches Governance Alignment
Mindcore helps organizations align cloud and network governance by:
- Assessing where trust is assumed instead of enforced
Across both network and cloud layers. - Mapping access paths end to end
From user identity to data access. - Reducing exposure through architectural changes
Not just policy updates. - Aligning governance ownership across teams
Eliminating responsibility gaps. - Prioritizing controls based on real risk
Not theoretical compliance.
The goal is governance that reflects how environments actually operate.
A Simple Governance Reality Check
Your governance model is misaligned if:
- Network controls do not apply to cloud access
- Cloud permissions are broader than network access
- Identity reviews are inconsistent across platforms
- Data access is governed differently in each tool
- Governance relies on documentation instead of enforcement
These are structural issues, not tooling gaps.
Final Takeaway
Network governance and cloud governance are not competing models. They are controls designed for different layers of the same environment.
Organizations that understand the difference can align them effectively. Organizations that do not end up securing the wrong layer while exposure grows elsewhere.