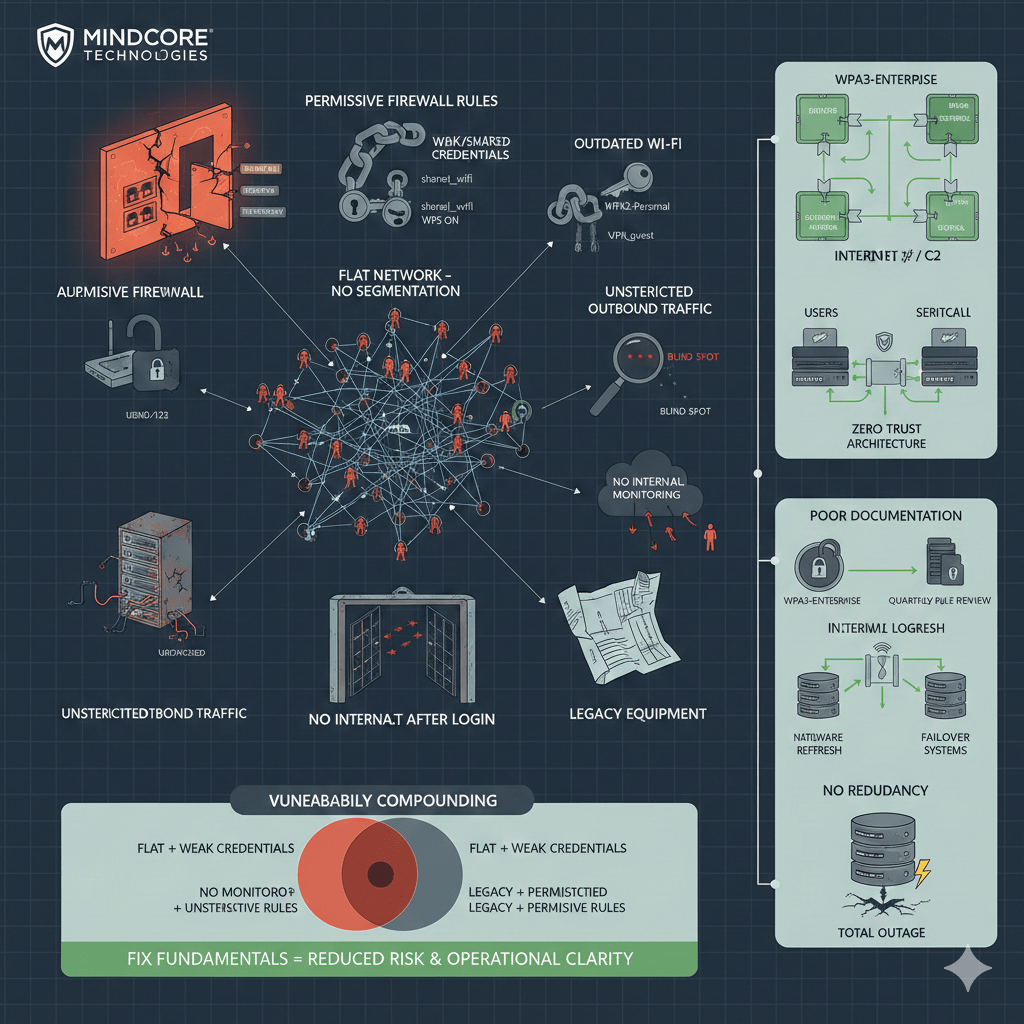
Most network breaches don’t happen because attackers are brilliant. They happen because networks trust too much, expose too much, and monitor too little. The same weaknesses show up repeatedly across industries, sizes, and environments.
At Mindcore Technologies, incident response almost always traces back to a small set of preventable network flaws. This guide cuts through generic advice and focuses on the vulnerabilities we actually see exploited—and the fixes that work in the real world.
1. Flat Networks With No Segmentation
The vulnerability:
Everything can talk to everything. Once attackers get in, they move laterally without resistance.
How attackers exploit it:
- Phishing delivers valid credentials
- Malware lands on one device
- Lateral movement spreads across servers and backups
- Ransomware encrypts at scale
The fix:
- Segment users, servers, and critical systems
- Restrict east-west traffic by default
- Use firewalls to enforce segmentation, not just perimeter rules
Segmentation turns breaches into contained incidents.
2. Overly Permissive Firewall Rules
The vulnerability:
“Temporary” allow rules become permanent. Ports and services remain exposed long after the business need is gone.
How attackers exploit it:
- Scan exposed services
- Abuse legacy access paths
- Bypass intended controls
The fix:
- Review firewall rules quarterly
- Remove unused or broad rules
- Enforce least privilege by service and destination
- Log and alert on unusual outbound traffic
Clean rules reduce attack surface immediately.
3. Weak or Shared Network Credentials
The vulnerability:
Shared Wi-Fi passwords, shared VPN accounts, or reused admin credentials.
How attackers exploit it:
- Credential reuse and leakage
- No way to revoke access per user
- Persistent access after employee departure
The fix:
- Eliminate shared credentials
- Use identity-based authentication (802.1X, SSO)
- Enforce phishing-resistant MFA for remote access
- Tie access to user identity and device posture
Identity beats passwords every time.
4. Unsecured or Outdated Wi-Fi
The vulnerability:
WPA/WPA2-Personal, WPS enabled, old firmware, guest and internal devices on the same network.
How attackers exploit it:
- Join the wireless network
- Blend in as trusted traffic
- Bypass perimeter controls
The fix:
- Use WPA3 or WPA3-Enterprise
- Disable WPS
- Separate guest and internal Wi-Fi
- Keep access point firmware current
- Monitor connected devices
Wi-Fi is part of the perimeter—treat it that way.
5. No Monitoring of Internal Traffic
The vulnerability:
Networks log nothing internally. Alerts only trigger at the edge—if at all.
How attackers exploit it:
- Operate quietly after initial access
- Move laterally using legitimate tools
- Exfiltrate data unnoticed
The fix:
- Enable internal traffic logging where feasible
- Monitor for abnormal behavior, not just signatures
- Correlate network, identity, and endpoint signals
- Alert on unusual data movement
Visibility is a prerequisite for response.
6. Unrestricted Outbound Traffic
The vulnerability:
Anything inside the network can connect anywhere on the internet.
How attackers exploit it:
- Exfiltrate data silently
- Maintain command-and-control channels
- Stage extortion without detection
The fix:
- Restrict outbound traffic to known destinations
- Block known malicious domains
- Alert on unusual outbound patterns
- Apply stricter controls to sensitive systems
Outbound control limits attacker leverage.
7. Legacy or End-of-Life Network Equipment
The vulnerability:
Old routers, switches, and firewalls running unsupported firmware.
How attackers exploit it:
- Known vulnerabilities with public exploits
- No security updates or patches
- Weak performance that disables inspection
The fix:
- Inventory network hardware
- Replace end-of-life devices
- Keep firmware updated
- Ensure hardware supports modern encryption and inspection
Unsupported gear is a liability.
8. Implicit Trust After Login
The vulnerability:
Once authenticated, users can access too much for too long.
How attackers exploit it:
- Abuse stolen sessions
- Move freely using valid credentials
- Avoid detection by looking “normal”
The fix:
- Enforce Zero Trust principles
- Limit access by role and context
- Use short-lived sessions
- Re-validate access continuously
Trust should be conditional, not permanent.
9. Poor Network Documentation
The vulnerability:
No one knows what talks to what—or why.
How attackers exploit it:
- Hide in undocumented access paths
- Abuse forgotten services
- Slow response during incidents
The fix:
- Document network flows and dependencies
- Maintain diagrams and inventories
- Review changes regularly
Clarity reduces both risk and downtime.
10. No Redundancy or Failover
The vulnerability:
Single ISP, single firewall, single point of failure.
How attackers exploit it (indirectly):
- Outages amplify business impact
- Recovery delays increase damage
- Pressure leads to risky decisions
The fix:
- Add backup internet or failover
- Monitor WAN and DNS health
- Test failover periodically
Resilience is part of security.
How These Vulnerabilities Compound
Most breaches involve multiple weaknesses, not one:
- Flat networks + weak credentials
- No monitoring + unrestricted outbound traffic
- Legacy equipment + permissive rules
Fixing even a few dramatically reduces risk.
How Mindcore Technologies Addresses These Gaps
Mindcore helps organizations remediate real-world network vulnerabilities through:
- Architecture and segmentation design
- Identity-aware access enforcement
- Secure Wi-Fi and remote access
- Firewall rule cleanup and optimization
- Internal visibility and monitoring
- Resilience and failover planning
We remove implicit trust and reduce blast radius by design.
A Quick Self-Assessment
Your network is vulnerable if:
- Internal systems communicate freely
- Access is shared or static
- Wi-Fi security is outdated
- Outbound traffic is unrestricted
- Monitoring is minimal
These issues are common—and fixable.
Final Takeaway
Common network security vulnerabilities are not exotic. They are structural. Flat networks, weak identity controls, poor visibility, and outdated equipment create predictable attack paths. The fixes are equally predictable—and effective—when applied intentionally.
Organizations that address these fundamentals reduce breach impact, improve uptime, and gain operational clarity. Those that ignore them continue to absorb avoidable risk.