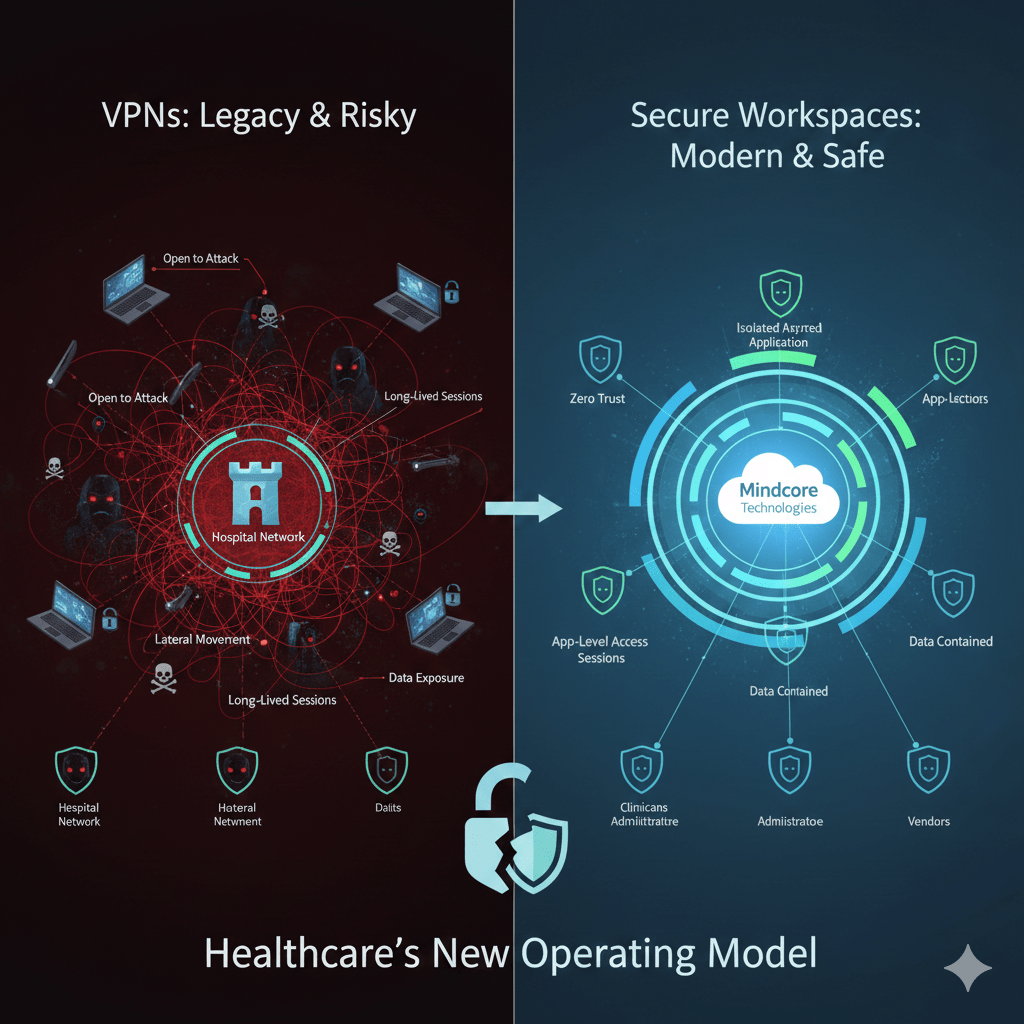
VPNs are not failing because they are misconfigured. They are failing because they were never designed for modern healthcare environments. Extending a trusted network to unmanaged endpoints, long-lived sessions, and third-party users creates risk that security teams can no longer contain.
Ransomware groups understand this. Auditors see it. Healthcare CISOs feel it daily.
At Mindcore Technologies, breach response and architecture reviews show the same root cause over and over: VPNs turn identity compromise into full network exposure. Secure workspaces exist to break that chain.
The Structural Problem With VPNs in Healthcare
VPNs operate on a simple premise: once a user authenticates, the network trusts them.
In healthcare, that premise collapses quickly.
- VPNs extend the internal network to external devices
Clinicians, administrators, and vendors effectively operate as if they are inside the network, even when connecting from home, hotels, or shared locations. - Authentication equals broad visibility
After login, users can often see far more systems than they need, increasing the blast radius of any compromised account. - Sessions persist too long
VPN connections remain active for hours or days, allowing attackers to reuse stolen sessions without reauthentication. - Credentials are reusable
Stolen VPN credentials provide repeatable access, not a one-time window.
Security teams are forced to defend an expanded perimeter instead of reducing it.
Why VPNs Are a Prime Target for Healthcare Attackers
Attackers do not break into healthcare networks. They log in.
VPNs are targeted because:
- Gateways are visible and constantly scanned
VPN endpoints advertise themselves publicly, inviting brute force, credential stuffing, and exploit attempts. - Credentials are harvested elsewhere
Infostealer malware collects VPN credentials long before attackers ever touch the network. - MFA is frequently bypassed through session theft
Stolen tokens and cookies render MFA irrelevant once a session is active. - Access looks legitimate
Monitoring tools see “authenticated users,” not attackers.
VPNs collapse identity compromise into full access.
What Secure Workspaces Change Fundamentally
Secure workspaces remove network trust from the access equation entirely.
Instead of extending the network, they:
- Isolate applications inside a controlled workspace
Systems are not directly reachable from user devices. - Grant access at the application level, not the network level
Users interact only with approved applications, not IP ranges or subnets. - Enforce session-based, identity-driven access
Each session is verified, scoped, and continuously evaluated. - Eliminate standing connectivity
Network paths exist only while access is explicitly approved.
This shifts security from perimeter defense to containment by design.
Why Secure Workspaces Fit Healthcare Realities Better
Healthcare environments require security that does not disrupt care delivery.
Secure workspaces support this by:
- Reducing attack surface without downtime
Applications remain accessible while infrastructure stays hidden. - Supporting remote and hybrid clinical workflows
Clinicians access systems securely without VPN complexity or performance issues. - Containing third-party access
Vendors and partners receive tightly scoped access without exposing the network. - Improving operational stability
Fewer network dependencies mean fewer points of failure.
Security aligns with clinical operations instead of fighting them.
How Secure Workspaces Limit Ransomware Impact
Ransomware thrives on lateral movement and visibility.
Secure workspaces disrupt both:
- No network scanning or enumeration
Attackers cannot discover systems because they are not visible. - No lateral movement paths
Compromised access is confined to a single application or session. - Data stays inside the workspace
PHI does not reach endpoints where it can be encrypted or exfiltrated. - Immediate session termination
Access can be revoked instantly without password resets or VPN reconfiguration.
This dramatically reduces dwell time and blast radius.
Why Secure Workspaces Improve HIPAA Compliance
HIPAA requires provable controls, not assumed trust.
Secure workspaces support compliance by:
- Enforcing least privilege by default
Users see only what they are authorized to access. - Providing application-level audit trails
Logs show exactly which systems containing PHI were accessed and when. - Reducing unnecessary exposure of PHI
Data remains contained within controlled environments. - Simplifying evidence collection
Audit data is centralized and consistent.
Compliance becomes an architectural outcome, not a manual process.
VPNs vs Secure Workspaces: A Practical Comparison
VPNs:
- Extend the network
- Rely on static trust after login
- Expose infrastructure
- Enable lateral movement
- Complicate audits
Secure Workspaces:
- Isolate applications
- Verify access continuously
- Hide infrastructure
- Contain compromise
- Simplify auditability
This is not an incremental improvement. It is a structural shift.
Why Healthcare Is Leading This Transition
Healthcare organizations are moving first because:
- Ransomware impact is immediate and severe
- PHI carries regulatory and reputational risk
- Remote access is unavoidable
- Legacy security models cannot scale
What healthcare adopts today becomes standard across regulated industries tomorrow.
How Mindcore Technologies Implements Secure Workspaces in Healthcare
Mindcore deploys secure workspace architectures by:
- Mapping clinical and administrative workflows
Access models reflect how teams actually work. - Replacing VPN-based access with application-level controls
Network exposure is removed from the equation. - Defining role-based access to PHI
Permissions align with job function and responsibility. - Enforcing device and session posture checks
Access adapts to risk in real time. - Providing centralized visibility and governance
Security and compliance teams maintain continuous oversight.
The goal is not disruption. It is measurable risk reduction.
A Simple Healthcare Reality Check
Your environment is still VPN-dependent if:
- VPN gateways are publicly reachable
- Network access follows authentication
- Sessions persist indefinitely
- Users can see systems they do not need
- Audits require manual reconstruction
These are architectural risks, not configuration errors.
Final Takeaway
VPNs solved a different problem in a different era. Today, they extend trust too far, for too long, across environments that cannot be controlled. Secure workspaces replace that model by removing network exposure, enforcing identity-based access, and containing compromise by design.
For healthcare organizations facing ransomware, compliance pressure, and permanent remote access, secure workspaces are not an upgrade. They are the next operating model.