Social Engineering
Social engineering is the art of manipulating, influencing, or deceiving you to gain access to your computer systems. Using human psychology, attackers play on human emotions such as fear or urgency to trick users into divulging sensitive information.

What is Social Engineering?
Humans are the weakest link in any cyber security program. Social engineering refers to a broad range of manipulation tactics used by hackers to acquire information from people. Once an attacker understands what motivates a user, they can effectively lure the target into exposing data, spreading malware, or giving access to restricted systems through social engineering. It is important to know the types of social engineering attacks, how to identify them, and how to prevent them so that your organization stays protected at all times.
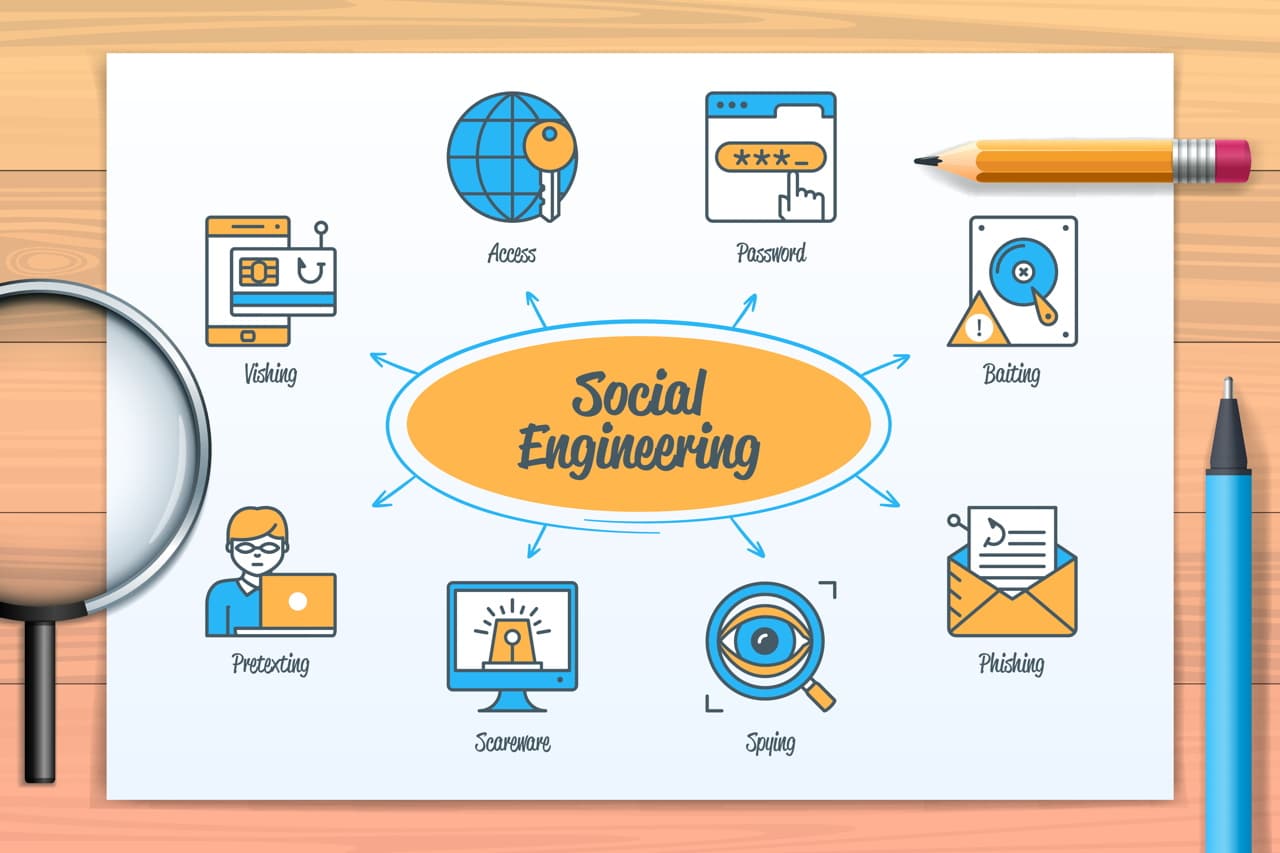

Types of Social Engineering Attacks
Cyberattacks almost always involve social engineering. These techniques typically involve email or text messages because they don’t require voice conversations. However, you can just as easily be faced with a threat in person. Some of the most common types of social engineering to look out for include:
Phishing
Phishing scams use fake emails to prompt a user to click on a malicious link. The communication appears to be from a legitimate source connected to the user, such as a C-suite executive. When the link is clicked, the user’s device or system becomes infected, and data is often compromised.

Vishing and Smishing
While phishing uses fraudulent email practices, similar techniques are practiced using communication methods such as phone calls and text messages. Vishing (or voice phishing) occurs when a hacker tricks the victim into disclosing information or giving access to their computer over the phone. Smishing (or SMS phishing) is done through SMS/text messaging.

Pretexting
Pretexting is a type of social engineering attack where an attacker creates a scenario to compel a victim to comply under false pretenses. In this attack, the bad actor may impersonate a police officer, investigator, or auditor to persuade the victim to follow their orders.

Baiting
Baiting is when an attacker uses something enticing or curious to lure a victim into a social engineering trap. A baiting scheme could offer a free music download or USB drive. Using the device or opening a malicious file can infect the victim’s computer, allowing the criminal to take over the network as soon as the file opens.

Tailgating and Piggybacking
Tailgating is a social engineering method that gains physical access to a building or other protected area. An attacker may tailgate another individual by sticking their foot or object into the door right before it shuts without being noticed. In a piggybacking scenario, the authorized user is aware and allows the attacker to “piggyback” off their credentials.

Quid Pro Quo
Quid pro quo, Latin for “something for something,” is when an attacker attempts to trade a service for information. For example, a hacker may call a company’s main phone line and pretend to be from the IT department. Once they reach a user who requires technical assistance, the hacker may convince the person to install malware or hand over sensitive data.

How to Identify Social Engineering
Social engineering comes in many forms via email, websites, voice calls, SMS messages, and even social media. Defending against social engineering attacks requires employees and users to practice self-awareness.
Attackers expect you to take action before considering the risks, so it’s crucial to slow down and think before doing anything or responding. If you receive a message with three or more of these traits, you are at a higher risk of being a victim of a social engineering scam.
Legitimate emails, phone calls, and texts arrive unexpectedly each day, but this is also a common tactic used by social engineers. Inspect the email address, caller ID, or social media profile carefully when getting a suspicious message.
In most cases, an attacker will ask the victim to do something they’ve never done before. The request can be to send money, open a document, execute a program, or send information. Being asked to do something out of the ordinary increases the risk of performing the request.
What are the chances of the requested action harming either the victim or the company if it were taken? If you are wary of the potential consequences, it’s probably a good idea to ignore the request. Ask the sender to prove their claimed identity, such as a co-worker or family member, before making a decision.
Most social engineering scams include a heightened sense of urgency. Known as a “stressor event,” the attacker may communicate a threat of harm (work, physical, financial, etc.) if the potential victim does not move quickly.
Phishing links are often used with social engineering to trick a user into installing malware on their device. Never enter credentials into a website directly from an email link. Look for irregularities in the URL, old or incorrect logos, and typos on the website.
How Can You Protect Yourself From Social Engineering
Businesses of all sizes are targets for social engineering, so it’s crucial to be proactive about your organization’s privacy and security. All employees must be aware of the signs and know the right steps to take when approached by a bad actor. Use the following policies and procedures to prevent a social engineering attack from negatively impacting your business.
Your Personal Identifiable Information (PII) is considered sensitive information and often used as a target for attackers. PII may refer to a user’s name, address, and birthdate, as well as their social security number and financial data. Do not ever share your PII with a third party.
Multi-factor authentication (MFA) adds an extra layer of security to your online accounts. MFA uses factors such as temporary passcodes, fingerprint identification, or facial recognition to verify your identity upon login. Implementing MFA makes it harder for an attacker to steal your information.
Once malware downloads onto your computer, it can steal your data, encrypt it so you can’t access it, or even erase it. Antivirus (AV) software keeps an eye on all the files that enter your system. Update this software on a routine basis to protect your data and devices.
If you receive a request for personal or company data, take all precautions to determine if it’s legitimate. Ask questions and verify the sender’s identity before complying with the request. You should also never engage with an email or link that looks suspicious or unfamiliar to you.
Employees need proper education on how to identify a social engineering attack. Regularly train your employees in security awareness using real-world examples of social engineering to prepare them for when an attack occurs.
Social Engineering Frequently Asked Questions
In simple terms, social engineering is a psychological attack against a company or organization that exploits people’s natural tendency to trust others. While hackers may develop different tactics to support their efforts, all social engineering attacks have the same goals: theft, fraud, or espionage. Generally, a social engineer attempts to fool someone into providing valuable information or access to that information.
In today’s world, all types of organizations are at risk of becoming victims of cyber attacks, including social engineering. However, some industries are more susceptible to these attacks than others. The industries most likely to be a target are small businesses, healthcare, government agencies, financial institutions, education, and energy and utility companies.
The best way to defend against social engineering is through security awareness training. Security awareness should be an ongoing activity at your company, whether it be on a monthly or annual basis. Employees might not be aware of the dangers of social engineering, or they may forget over time. Conducting security awareness among employees, and keeping them refreshed, is the first line of defense against such attacks.
Phishing is the most common method of social engineering. According to APWG’s recent Phishing Activity Trends Report, phishing scams hit an all-time high in 2021, with more than 300,000 attacks recorded in December. Social engineers use phishing so often because these scams are difficult to detect, as the malicious email is convincing and impersonates a trusted source known to the target.
Social engineering is one of the most successful ways to obtain sensitive information. It doesn’t require nearly as much effort or technical skill to penetrate a defense’s walls. Social engineering preys on human error, which accounts for 95% of all cyber attacks. It’s often easier to exploit people through social engineering than to find a network or software vulnerability.