The world of work is changing. It used to be that work was a place. Not anymore.
Today, it’s an increasingly dynamic activity, where people expect the experience to be as mobile and adaptable as they are. People are trading in cubicles and desktops for virtual meetings and mobile devices.
To power this new way of working and support strategic business objectives, organizations have embraced user-friendly SaaS and cloud-based services.
Problem is, managing a proliferation of apps and data scattered across clouds and data centers can be clumsy and chaotic. If improperly managed this will become a security risk and will put a strain on productivity.
Traditional security perimeters built around the corporate data center worked as long as apps, data, and employees were all behind the corporate firewall.
As work extends beyond the firewall to include virtual, web, and SaaS apps, the old way of layering fragmented solutions is no longer enough to keep you ahead of ever-evolving threats.
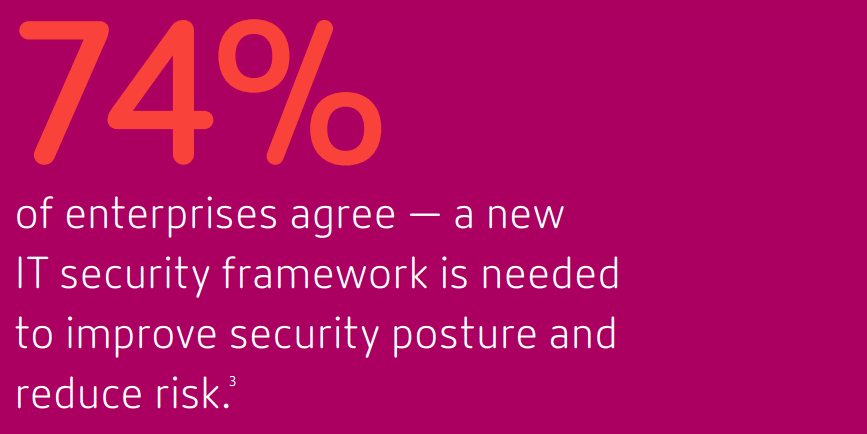
Now, new security framework is needed to secure your apps and data across the clouds, devices, and networks where business is happening, and people are collaborating.
This post covers how to simplify security in a cloud-first world, how to create a people-centric security approach, the trusted framework for securing the digital workspace, and essential elements of a secure digital perimeter.

Simplifying security in a cloud-first world
A confident security strategy can help you see opportunity — not vulnerability — in a rapidly expanding array of devices, apps, services, and cloud infrastructure.
A holistic approach gives you the flexibility and control to balance security risk with the need to advance innovation, growth, and new ways of working.
A secure digital workspace is a contextual, integrated way to deliver and manage the apps, desktops, data, and devices your users need to be productive. It can fully aggregate all apps and data — both on-premises and cloud — to deliver the right experience to the right user at the right time.
Protected by a secure digital perimeter that surrounds users wherever they are, a digital workspace gives IT, security, and networking teams simplified control and proven security across today’s hybrid, multi-cloud, and SaaS environments.
A secure digital workspace will unify everything
Apps and desktops:
Secure, remote access to web, SaaS, and virtual applications and desktops from any device.
Unified endpoint management:
Full access to mobile device management (MDM), mobile application management (MAM), mobile content management (MCM), secure network gateway, and enterprise-grade mobile productivity apps.
Data:
Access, sync, and securely share files from any device, with full control for IT.
Networking:
A secure digital perimeter provides reliability, performance, analytics, and security for apps deployed in the data center, cloud, or delivered as SaaS.
A people-centric security approach
In the same way a digital workspace provides access to apps and data from anywhere, the network perimeter must dynamically expand beyond the data center to protect information and users wherever they are. Our modern, people-centric approach for apps deployed in the data center, cloud, or delivered as SaaS gives you:
Simplified control:
• People-centric policies based on identity
• Centralized management and distributed policy enforcement across various control points — apps, content, devices, networks — in hybrid and multi-cloud environments
• Protection of application infrastructure by hiding or minimizing attack surfaces
• Easily enabling compliance to regulatory standards
360-degree visibility:
• Full visibility across your entire infrastructure
• Recording and aggregating logs and transaction flows between users, apps, devices, content, and networks
Intelligent analytics:
• Providing insights by analyzing patterns for cyber threats, app and network performance changes, infrastructure usage, and user behavior anomalies
• Triggering of automated policy-based actions for access control, threat management, IP protection, and high availability
Trusted framework for securing the digital workspace
• Deliver an on-demand people-centric security perimeter
• Minimize and hide attack surfaces
• Get full visibility across SaaS, hybrid, and multi-cloud environments
• Automate contextual actions and policies based on triggers
• Share threat intelligence across services to prevent malicious actions and behaviors
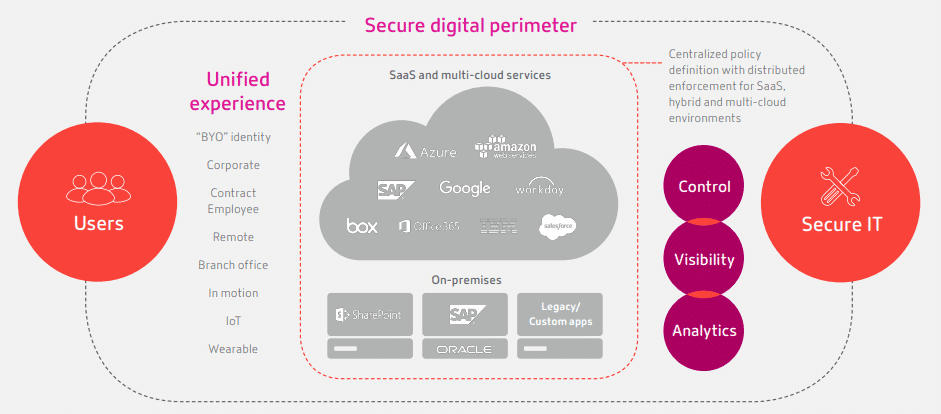
Essential elements of a secure digital perimeter
Contextual and secure access
User identity is core to a people-centric approach. Deliver a simple, personalized experience to each user based on context and preferences. Set contextual policies to automatically adapt to changing conditions—grant or revoke access based on the user, location, device, or suspicious activity. Provide single sign-on (SSO) across web, SaaS, and virtual apps to simplify IT management and provide a better user experience.
Mobile and device security
Enable your mobile workforce and secure corporate and BYO devices by seamlessly applying device and app control policies. Provide end-to-end encryption to secure data as it moves between the endpoint, network, and company resources. Leverage sophisticated container technology to secure apps and data on the device with a high-security encrypted vault for key storage.
Reduce exposure to insider and outside threats
Because you have visibility across endpoints, the network path, web traffic, data repositories, and web, virtual, and SaaS applications, it’s easier to detect malware. Isolate high-target apps to protect them against attacks. Inspect browsing activity and redirect suspicious site access to a safer, sand-boxed location to prevent any malicious activity or harmful data from entering the perimeter. Using policies, you can centrally control and manage blocked sites.
Secure collaboration with data security and intellectual property (IP) protection
Secure your most sensitive business data, whether it’s in use, in motion, or at rest in the data center or the cloud. Exchange and collaborate on documents easily and securely while ensuring industry-standard AES 256 encryption of all meta-data and content. Integrate with data loss provider (DLP) solutions for visibility and control over the sharing of sensitive data.
Governance, risk, and compliance
Easily demonstrate compliance with visibility across your entire infrastructure. Better enforce compliance and governance aspects such as information rights management (IRM) and data loss prevention (DLP) by integrating users’ roles and responsibilities directly into how they use and interact with apps and data. This makes it easier to detect and prevent external or internal malicious attempts to steal sensitive data.
Business continuity
Create a more coordinated approach to application security by gathering input from the network and from web, virtual, and SaaS apps. Ensure the availability and performance of apps and services to users at all times through always-on connectivity, even during server or network outages, and protection against attacks that aim to disrupt business operations.
The freedom to innovate
Mindcore can help you enable all the ways your employees want and need to work, while you can remain confident that your data, apps, and network are secure. Engineered to empower IT with control and users with flexibility, our comprehensive security approach gives you the freedom to adopt new innovations that will advance your business priorities and support new ways of working with confidence.
Ready to get started? Dial 973-664-9500 ext 1 and a security specialist will help you right away.

