Dispersive
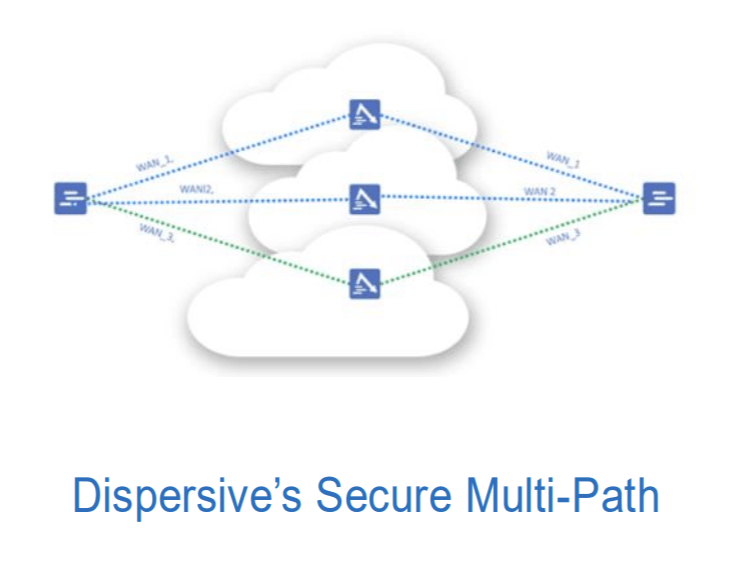
Dispersive delivers unbreakable, self-healing connectivity built from DARPA innovation. Using Automated Moving Target Defense, it constantly shifts, encrypts, and splits your data so attackers can’t even find the target — let alone breach it. It’s the only preemptive, quantum-ready network solution that hides in plain sight.
Mindcore Secure Workspace Solutions Powered by
Tehama Technology

Awarded Global Top 250 MSSP 2024

Schedule Your Free Consultation
Deployment & Support
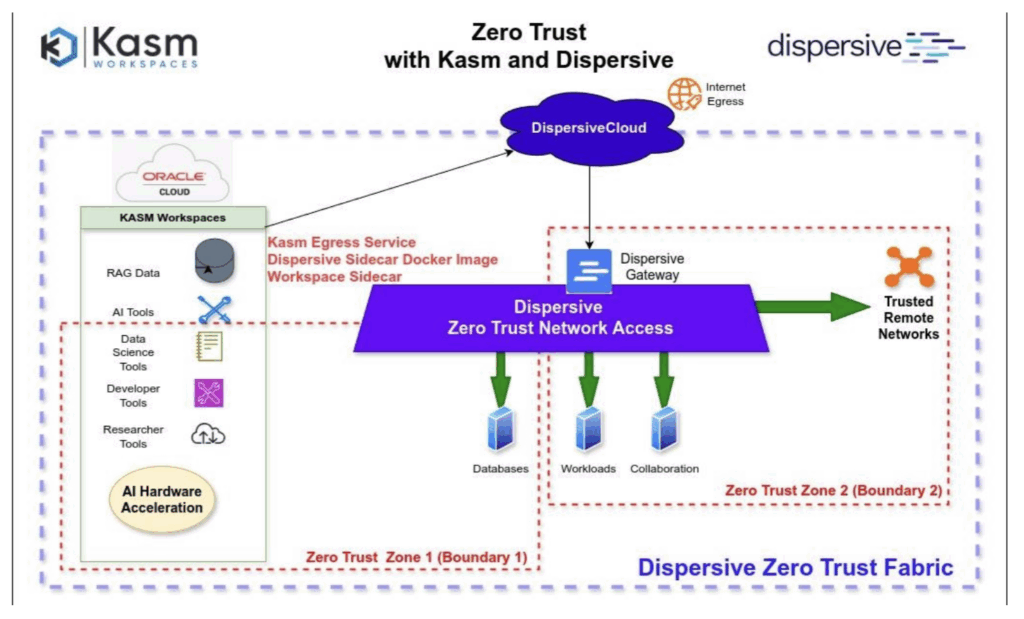
Deployment Models
- Dispersive Cloud (SaaS) – fully managed by Dispersive.
- Dispersive Fabric – self-managed model.
- Client Software – for remote or mobile users.
- Gateways can be virtual or physical (Lanner 1513/1515 series).
Support Model
- Onboarding via Zendesk portal with training and ongoing success check-ins.
- Two support tiers: business-hours (standard) and 24/7 (premium).
- Designed to be largely “set-and-forget” once deployed.
Use Cases
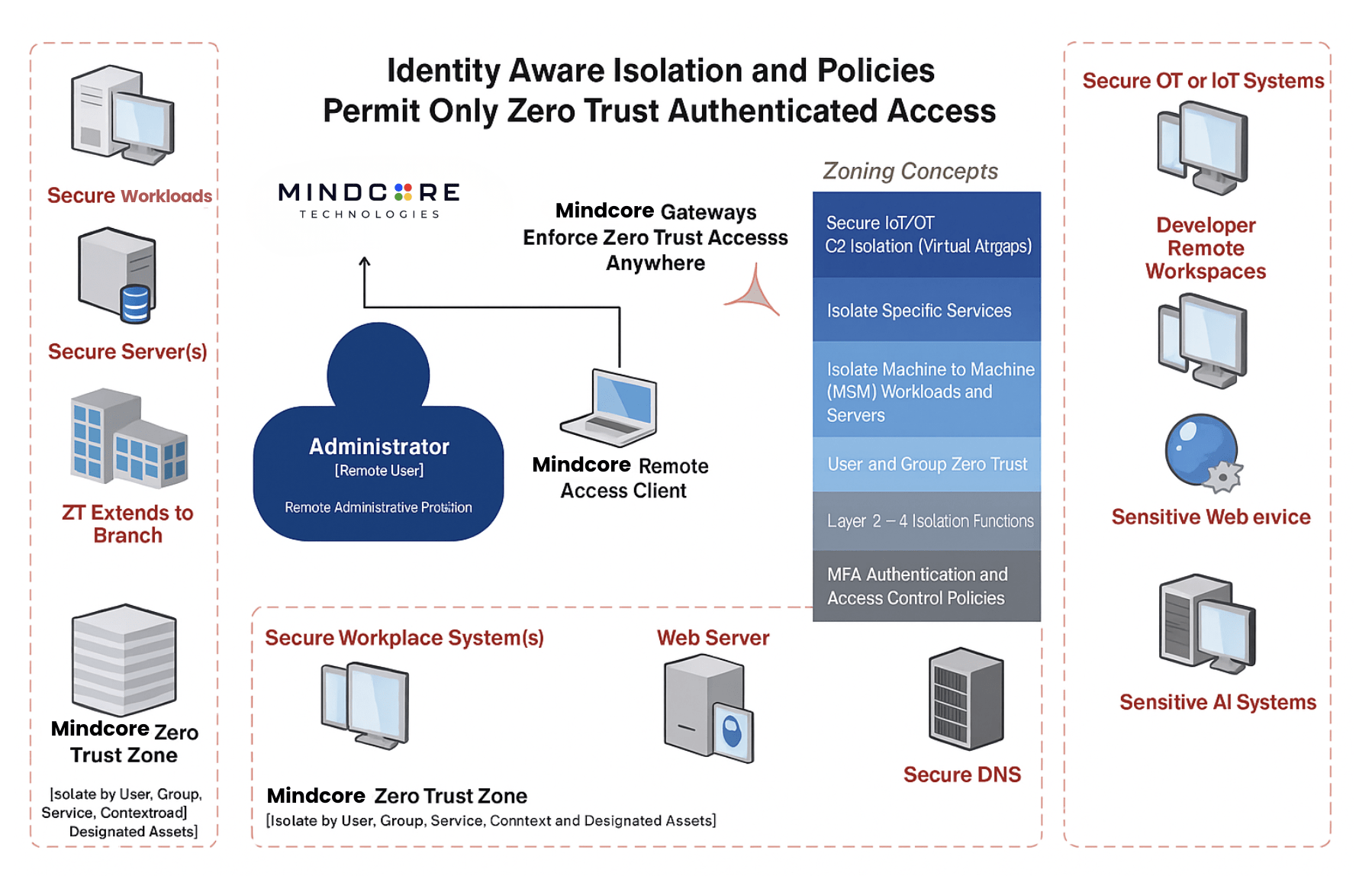
- Zero Trust Access for healthcare, finance, and enterprise networks.
- Cloud WAN and Secure Remote Access (especially for hospitals with distributed users).
- AI Isolation: protects model inference data and prompts from IP theft.
- IoT & Camera Protection: improves latency and secures live feeds.
- Satellite/5G Optimization: reduces latency by 30–40% even over high-latency links (e.g., Starlink).
- CrowdStrike Integration: automated risk-based network isolation (removes risky users dynamically).