Social engineering is the art of manipulating people to give up confidential information. These exploits have been around long before the rise of the internet and computers. Criminals use social engineering tactics because, unlike software or hardware hacks, exploiting your natural tendency to trust is much easier. We will discuss what social engineering is, the different types of social engineering, how to recognize a social engineering attack, and tips to avoid becoming a victim of social engineering scams in this post.
What is Social Engineering?
Social engineering is a form of manipulation that exploits human error to attain private information or access to valuables. This “human hacking” scam tends to lure people into giving access to restricted systems, spreading malware infections, or exposing data. Social engineering attacks are built around how people think and act and what motivates the person’s actions to understand the user better in order to effectively manipulate them. These attacks can happen online, in-person, or through other interactions. Common forms of social engineering are phishing, business email compromise, vishing, pretexting, and SMiShing.
Types of Social Engineering Attacks

Business Email Compromise
Business email compromise happens when an attacker takes over someone’s email account, either by purchasing the login credentials on the dark web, cracking the password, or phishing the information. The attacker will send emails to individuals on the account’s contact list — these emails may contain links that spread malware when clicked. This is particularly concerning because users are highly likely to click a link sent to them from a friend or coworker.
Phishing
Phishing scams are used to trick people into giving out personal information such as bank account numbers, passwords, and credit card numbers. Phishing emails will often prompt a victim to click a link or sign into one of their web accounts. When clicked, the link will take them to a site that looks legitimate, but has a slightly different address. Once the victim logs in, the scammer has access to the credentials and will use them to carry out fraudulent activities.
Pretexting
Pretexting is when an attacker creates a fictional backstory to influence the behavior of the victim and get them to hand over valuable information. For example, the attacker may pose as a representative of a survey firm and ask you a few questions. When the pretexter has the information they need, they use it to call companies with whom you do business and pretend to be you or someone with authorized access to your account.
SMiShing
Where phishing uses emails and vishing uses phone calls, SMiShing uses text messages to exploit the victim. SMiShing is usually more effective than other phishing attacks because people tend to trust a text message more than an email. A typical SMiShing scam will tell a user they are going to be charged daily for a made-up service, providing a link to opt out of the service and avoid the charges and ask for your personal information to submit your preference.
Vishing
Vishing, or “voice phishing”, is a phone scam that relies on convincing victims that they are doing the right thing by responding to the caller. The caller will often pretend to be a government agency, tax department, police, or the victim’s bank. A second tactic is to leave threatening voicemails that tell the recipient to call back immediately or they risk being arrested, having bank accounts shut down, or worse.
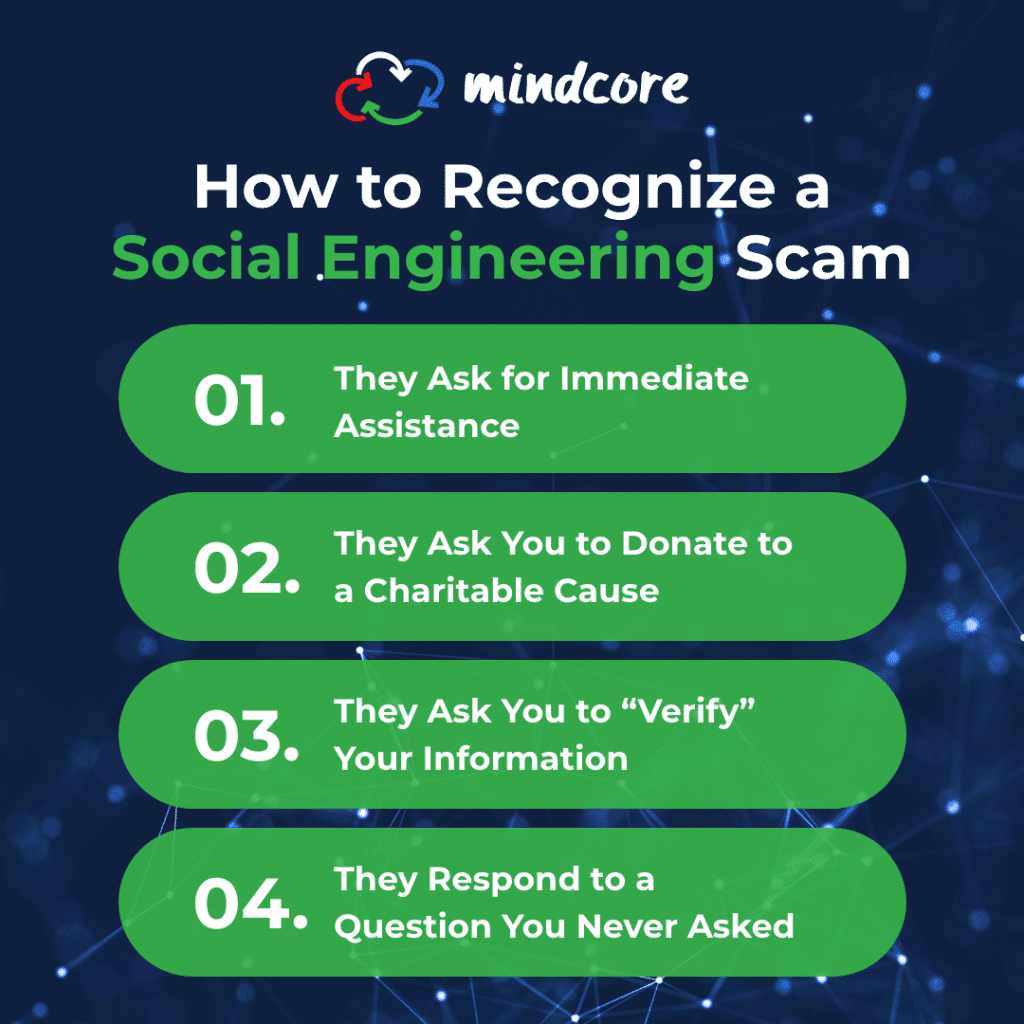
How to Recognize a Social Engineering Scam

Asking for immediate assistance
Social engineers will use language that instills a sense of urgency, trying to pressure the victim to rush into action without thinking. If someone asks you to make an urgent wire transfer, ensure that the transaction you’ll be conducting is legitimate.
Asking you to donate to a charitable cause
Preying on kindness and generosity, social engineers may request donations to charitable organizations. By researching you on social media, social engineers can find out which charities, disaster relief efforts, or political campaigns you are likely to support.
Asking you to “verify” your information
Another approach social engineers will take is presenting a problem that requires you to “verify” your information by clicking on the displayed link and providing information in their form. The link location may look legitimate with all the right logos and branding.
Responding to a question you didn’t ask
Social engineers may pose as a customer service agent from a company you do business with and send a message “responding” to a request for help. Even though you didn’t ask a question originally, you might take the opportunity to receive support for an issue you’ve been experiencing.
How to Prevent Social Engineering

Identify your valuables
Be aware of what information you have that is valuable to hackers and make sure it is well protected. Your organization’s “crown jewels” may be physical assets or intangibles like patents or intellectual property.
Verify Identities
If an email looks like it is from a company you use, do your own research. Be suspicious of any unsolicited messages and call the sender directly to confirm if they did send you the message in question.
Slow down
Scammers want you to act first and think later. Slow down, evaluate the situation, and identify any potential red flags before rushing into anything.
Verify links before clicking
Some phishing scams use shortened links, such as a bit.ly link, which may be covering up a malicious URL. Stay in control by finding the website yourself using a search engine to ensure you land where you intended to.
Educate users
To prevent social engineering attacks, you need to generate knowledge and awareness around the issue. Make sure users are up-to-date on social engineering threats so they can take the necessary steps to keep your organization safe.
Email protection software
Email protection software is used to examine incoming messages for signs of malware, malicious intent, and impersonation attempts and stop them from ever reaching your network.
Protect Your Organization’s Assets with Mindcore
Mindcore provides New Jersey and Florida companies with the cyber security they need to stay productive. Our full range of cyber security services and 24/7 support will prevent unwanted threats and ensure that you’re prepared for any situation that may arise. Contact us to schedule a consultation with one of our IT specialists today.