Amid a global pandemic and political unrest, cyber attacks have maintained prevalence. Since the start of the pandemic, ABC News reported a staggering 600% increase in malicious websites. In December 2016, it was estimated that every 40 seconds a business falls victim to a ransomware attack — this year, it’s every 11 seconds. Despite this fact, the timing of an attack may be unclear from a victim’s perspective. It’s important to know the methods of entry, common tactics, and timeline of specific events to understand the nature of ransomware attacks and isolate when they are set to happen.
Ransomware Military Tactics
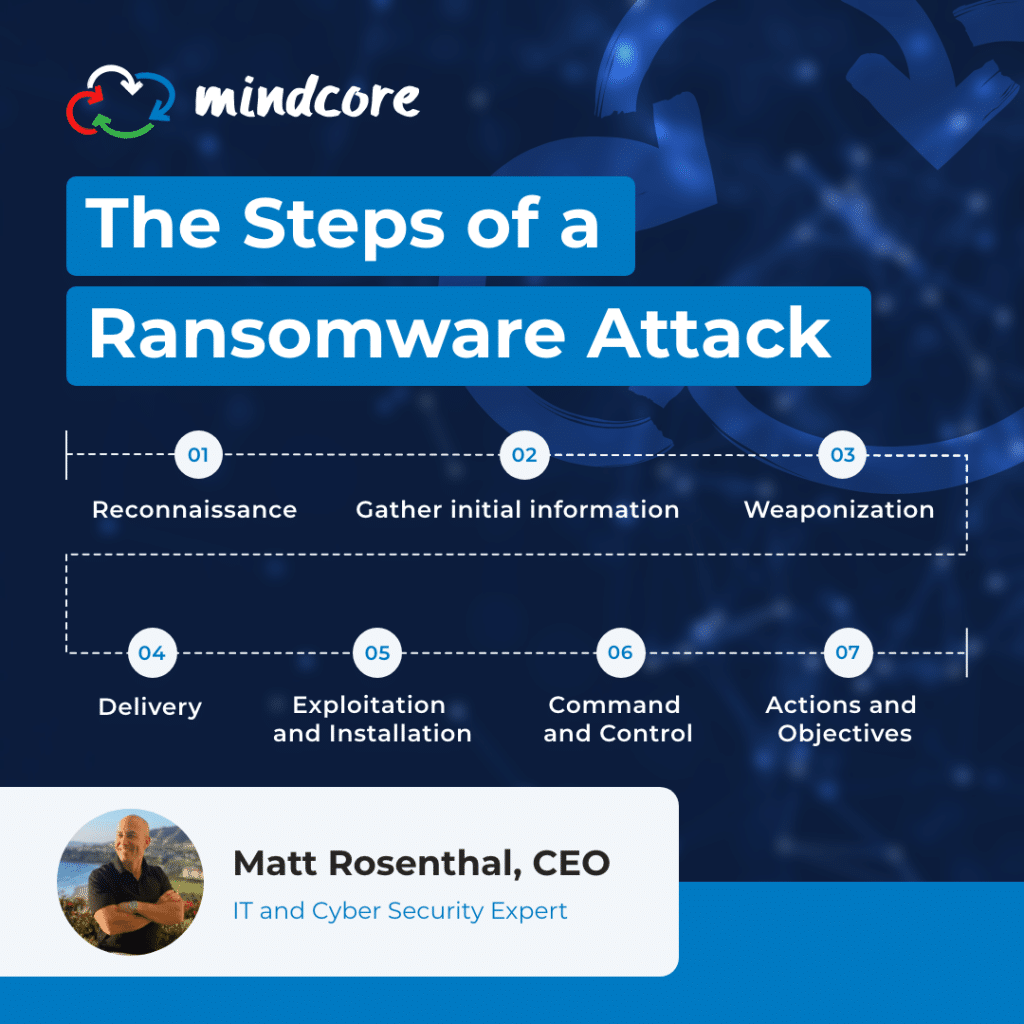
Ransomware is a form of malware that encrypts files as a way of extortion. The attacker demands a ransom from the victim to restore access to their important data, increasing their chances of a successful payoff. Generally, ransomware attacks are carried out by cyber threat actor groups, which are human-operated ransomware distributors using unique messaging to target and persuade their victims. Threat actors use a series of events over several days, or even months, that allows them to execute their crime and infiltrate a network. They follow a proven intel process, including the following to steps to extort their victims:
Reconnaissance
Reconnaissance is the preliminary step in any ransomware attack. Hackers identify a vulnerable target and gather the information needed to discover weaknesses and security vulnerabilities. There are two types of reconnaissance — active and passive. The process of reconnaissance typically involves these seven steps:
- Gather initial information
- Determine the network range
- Identify active machines
- Discover open ports and access points
- Fingerprint the operating system
- Uncover services on ports
- Map the network
Weaponization
During the weaponization phase, the hacker uses the previously gathered information to find ways to get into the target’s network. This could involve creating spear-phishing emails or “watering holes,” which are fake websites that look identical to a known vendor’s or other business contact’s web page. Hackers also collect the tools necessary to successfully exploit any vulnerabilities found once they gain access to the network.
Delivery
The delivery phase is when the attack becomes visible to the victim. Phishing emails are sent, “watering holes” are posted to the internet, and the hacker waits for the arrival of all the data they need from the victim. If a phishing email contains a malicious link or attachment, the hacker waits for a user to “click here” and the malware is delivered.
Exploitation and Installation
As usernames and passwords arrive, the hacker tries them against web-based email systems or virtual private network (VPN) connections to the company network. If malicious attachments were sent, the hacker can access the affected computers remotely. Now, they can explore the targeted network to determine the traffic flow, what systems are connected to it, and how to exploit them.
After establishing their presence, the hacker installs a persistent backdoor, creates administrator accounts on the network, and disables firewall rules. This ensures that they will have consistent access to the network over an extended period of time.
Command and Control
Once the network has been compromised and malware is running on the affected systems, all required tools are in place for the command and control phase. The hacker can look at anything, impersonate any user on the network, and even send emails from the CEO to all employees. They can also lock a company’s IT users out of the entire network, perhaps demanding a ransom payment to restore access.
Actions and Objectives
The last phase of a ransomware attack is when the hacker achieves their objectives. This could be stealing employee, customer, and product design information or disrupting the target company’s operations as a whole. Cyber threat actors lurk and purposely go unnoticed for as long as they need before they determine a course of action.
Known Infiltration Tactics
Ransomware delivery methods haven’t changed much over the years. In 2019, 92% of all malware was distributed through email. Cyber threat actors are also still using phishing campaigns with malicious links or attachments, open RDP ports, unpatched operating system vulnerabilities, and unpatched software to carry out an attack. Luckily, cyber security best practices are still effective in protecting networks even if ransomware attacks may appear more often than before. Generally, best practices involve looking out for emails that attach unexpected documents, request private credentials, or offer prizes or money rewards. Even if they appear to be from a legitimate organization or trusted source, do not trust them or take action to prevent an attack.
How to Prevent Ransomware Attacks
Defending against ransomware requires a holistic approach that brings together your entire organization. There are proven techniques that can help stop attacks and limit the effects of ransomware.
- Always confirm that requests sent to your inbox are legitimate
- Change default passwords to enhance the security of home networks
- Maintain a healthy amount of skepticism
- Use multi-factor authentication on all devices and apps
Cyber Security Solutions for Ransomware at Mindcore
Every company in New Jersey and Florida faces constant threats to its network security. Mindcore provides comprehensive cyber security services to help protect your critical data and systems against malicious attacks. Please contact us today to schedule a consultation with one of our cyber security experts and to learn more about our ransomware solutions.