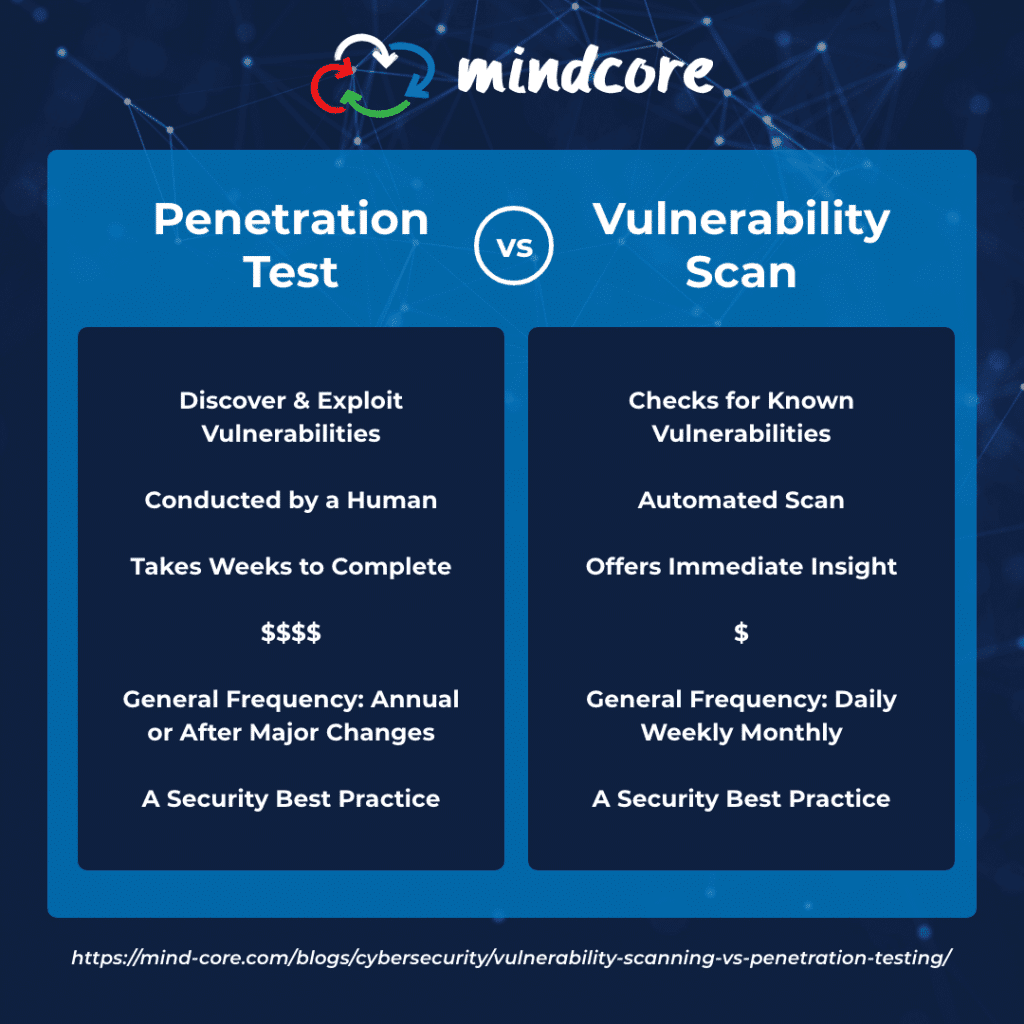
Penetration testing and vulnerability scans are two different ways to test your IT systems for vulnerabilities and weaknesses. Many companies often confuse penetration testing and vulnerability scanning as the same service. However, the two cyber security services are different from each other but go hand in hand.
What is Penetration Testing?
A penetration test is a detailed examination by a real person that actively exploits weaknesses in your IT system. It stimulates a hacker attempting to get into a business’s IT system through hands-on research and exploiting vulnerabilities. Analysts, also known as ethical hackers, search for vulnerabilities during the test and then try to prove that they can be exploited, compromising and extracting data from your network in a non-damaging way.
Penetration testing is an extremely effective approach to identifying and remediating vulnerabilities, providing a detailed report that offers a deeper look into your organization’s data security. The report includes descriptions of the attacks used, testing methodologies, and remediation recommendations. Although penetration tests may be expensive and take more time to complete, they provide more accurate and thorough results.
What is Vulnerability Scanning?
Vulnerability scans, also known as vulnerability assessments, are an automated, high level test that identifies potential and known vulnerabilities in network devices, such as firewalls, routers, servers, and applications. Generally, vulnerability scans are run by software and performed regularly to maintain information security and identify missing patches or outdated security protocols. A detailed report is created after the vulnerability scan is complete, generating an extensive list of vulnerabilities found and references for further research on the vulnerability.
Vulnerability scans are more of a passive approach as they do not go beyond reporting detected vulnerabilities. Sometimes a scan may identify potential weaknesses that may be a false positive, identifying a false threat. However, good vulnerability assessments rank vulnerabilities into risk groups from low to high and assign a score to the vulnerability, allowing you to focus on the highest potential risks. Although there may be some limitations to a vulnerability scan, it’s necessary to keep your IT system secure and an affordable and automatic test that is quick to complete.
What is the Difference Between Penetration Testing and Vulnerability Scanning?
The main thing that differentiates penetration testing from vulnerability scanning is the human element. Penetration tests are not automated and are conducted by human beings instead of being run automatically by software. While vulnerability scanning offers immediate insight, penetration tests may take weeks to complete to rule out any false positives. Vulnerability scans are great if you want a weekly or monthly report on your network security, while penetration tests are an extremely thorough way to deeply examine your business’s IT cyber security. However, both tests work together to ensure optimal IT security. The two services each have a different and important role to play to reduce your company’s cyber security risks.
Cyber Security Company in NJ & FL
Mindcore is a cyber security company in New Jersey and Florida that offers a wide range of cyber security services, including penetration tests and vulnerability assessments. We offer your employees training on our security tools in order to give your company a good security posture and reduce unnecessary time spent on troubleshooting. Please schedule a consultation with us today to learn more about our penetration testing services and vulnerability scans.

